-
Notifications
You must be signed in to change notification settings - Fork 1
Security Hijack
Security Access is a service that is used to authenticate a tester (e.g. a servicing tool, or another ECU) to a given ECU. The ECU is queried for a challenge (the seed), sends the seed and receives a response (the key) from the other party.
With Security Access Hijack, a man-in-the-middle (MITM) attack is performed on both parties. The attacker doesn't know how to calculate the key, however the attacker can intercept communications between the ECU and the tester. In the following picture, you can see the attack in sequence:
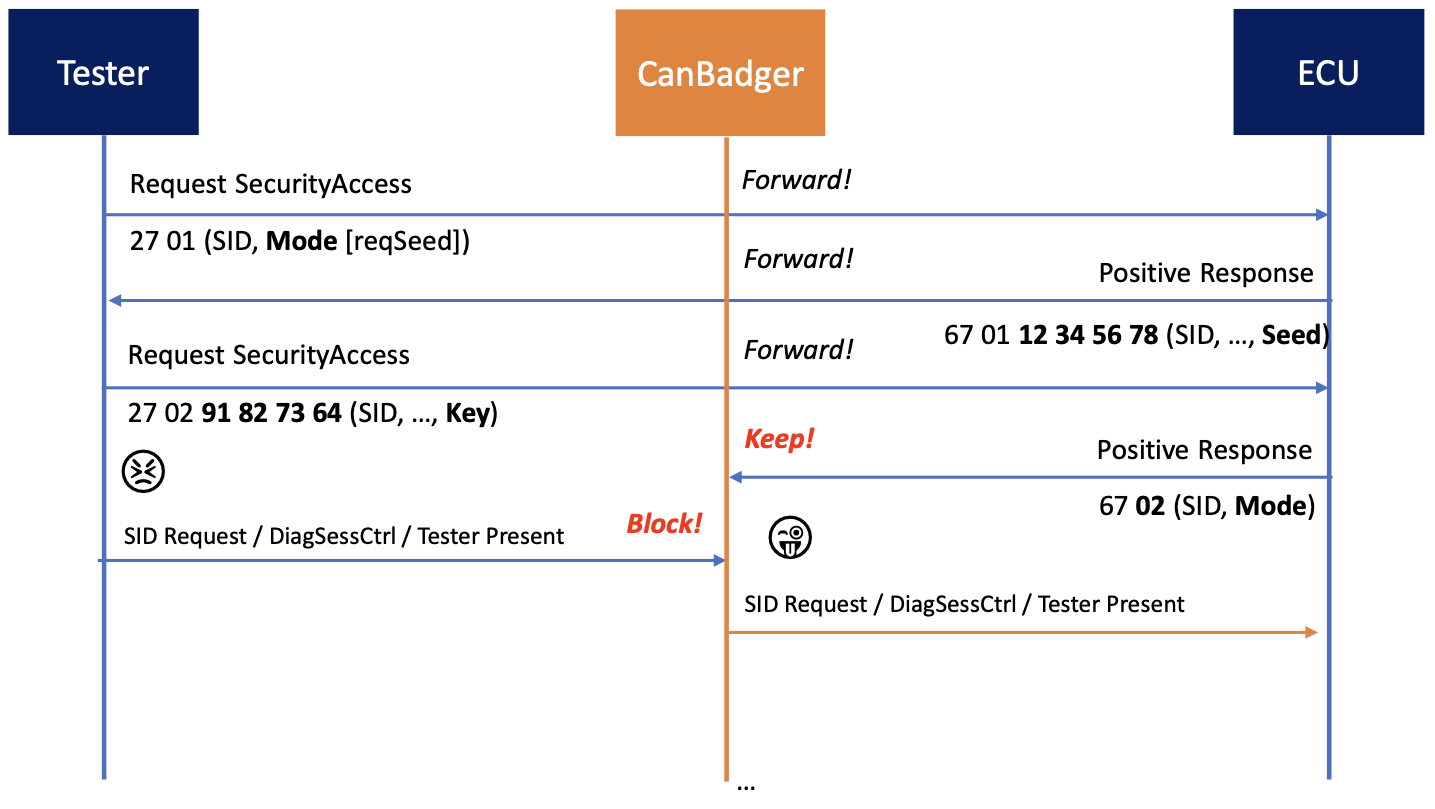
The attacker uses the tester to receive the key, but then disconnects the tester once the ECU gives a positive reply to the supplied key. Then, the attacker is in full control of the session. It follows that attackers don't need to have knowledge of the seed/key algorithms in order to perform advanced attacks.
It was initially demonstrated with UDS, however the CANBadger has implementations for UDS, TP2.0 and KWP.
Visit our website for more information, customized automotive security hardware or trainings.