-
Notifications
You must be signed in to change notification settings - Fork 67
How to Use
shusei tomonaga edited this page Apr 22, 2019
·
1 revision
MalConfScan has two functions malconfscan and malstrscan.
malconfscan can dump the malware configuration data, decoded strings or DGA domains.
$ python vol.py malconfscan -f images.mem --profile=Win7SP1x64
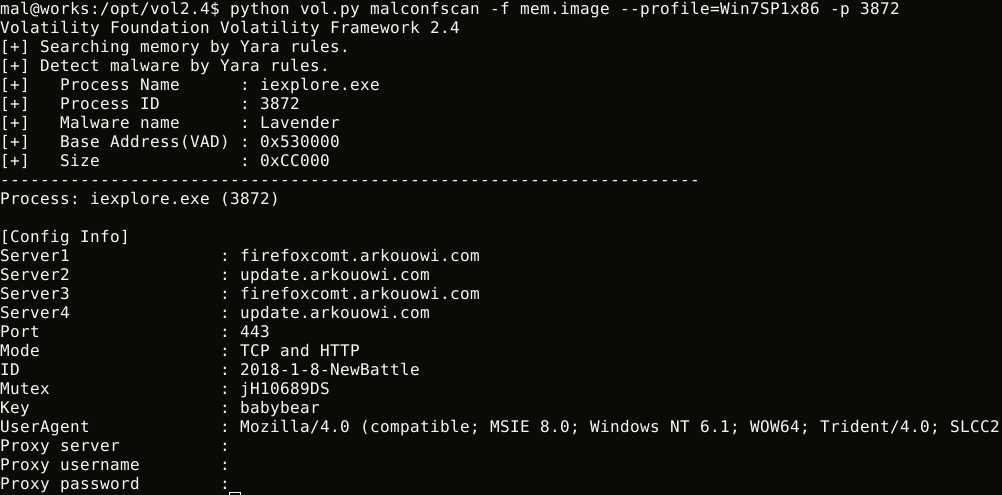
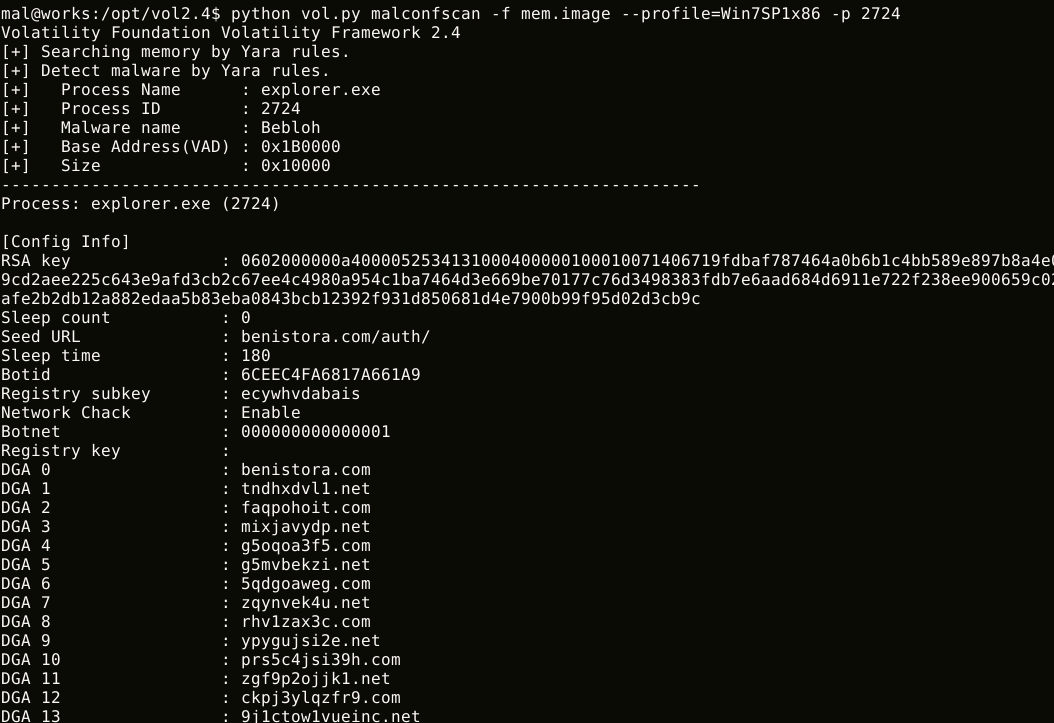
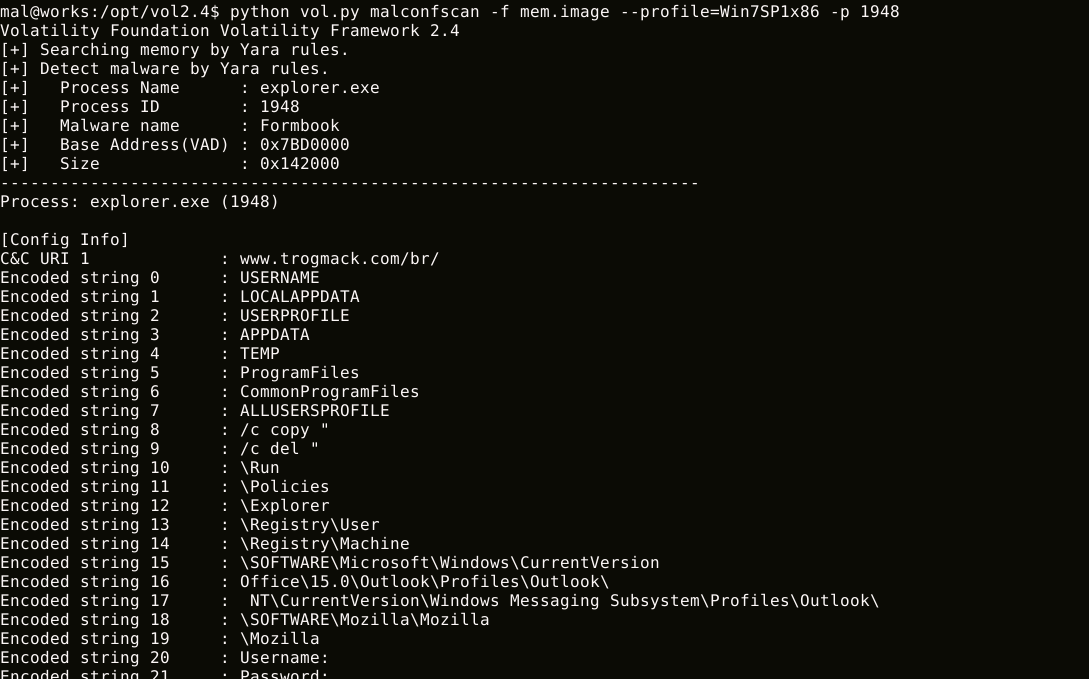
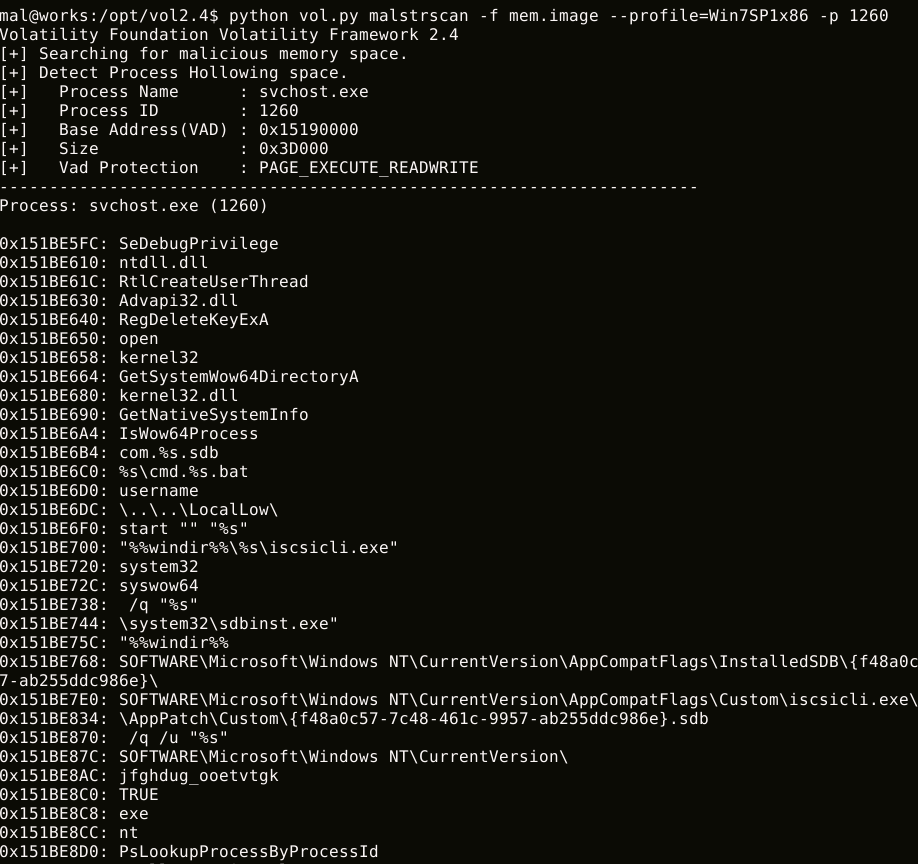
malstrscan can list strings to which malicious code refers. Configuration data is usually encoded by malware. Malware writes decoded configuration data to memory, it may be in memory. This feature may list decoded configuration data.
This feature lists strings only from PE loaded memory space by default. -a option will also list strings in the parent memory space, such as Heap.
$ python vol.py malstrscan -a -f images.mem --profile=Win7SP1x64