A Discourse plugin to enable LDAP/ActiveDirectory authentication.
Checkout: Installing a Plugin.
After the plugin is installed, logging in as an Admin and navigating to admin/site_settings/category/plugins will enable you to specify your LDAP settings. Most of the configuration options are documented in omniauth-ldap.
By default, user accounts are automatically created (if they don't already exist) after authentication using name, nickname and email attributes of the LDAP entry. If you do not want this behavior, you can change the ldap_user_create_mode configuration value to one of the following:
| Name | Description |
|---|---|
| auto | Automatically create a Discourse Account after authenticating through LDAP if account does not exist (default). |
| list | Provide a list of users in ldap_users.yml. Will only create an account and pass authentication if user with email is in list. See example ldap_user.yml. |
| none | Fail auth if the user account does not already exist. This is a good option for an Admin that creates accounts ahead of time. |
list also allows the specifying of User Groups, which will be automatically assigned to the user on creation. It also allows specifying a different username (for local account) and name for the Discourse User Account than what is returned in the LDAP entry.
The Lookup Users By Attribute setting specifies how to to link the LDAP response entry to a user within Discourse. By default, it uses the email attribute in the LDAP entry to try and find an existing Discourse user. If email address is unlikely to change for a given user, it is a good idea to keep this default setting.
If, on the other hand, LDAP email address has the possibility of changing, setting Attribute to lookup users by to username is the way to go to avoid "de-linking" the Discourse User from its corresponding LDAP entry.
The only possible values are email or username.
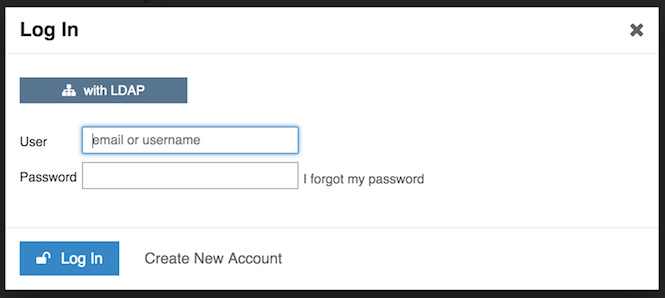
When disabling Local Login and other authentication services, clicking the Login or Sign Up button will directly bring up the LDAP Login popup.
Make sure coding style is maintained and all tests pass by running:
rspec
0.6.1- Bump net-ldap dependency version in order to support Ruby 3
0.6.0- Update omit_username to override_username following Discourse core changes
0.5.0- Remove call to deprecated Discourse code from FEATURE: Use full page redirection for all external auth methods
0.4.1- Make LDAP Password field secret
0.4.0- Fix Undefined variable: "$fa-var-sitemap" error when upgrading to Discourse version > 2.2.0
0.3.8- Fix enabled? undefined warning
0.3.7- Add Attribute to lookup users by Setting
0.3.6- Fixed bug where user who changed email can no longer be looked up
0.3.5- Updated styling of LDAP login popup
0.3.0- Fixed typo to ldap_bind_db configuration name
0.2.0 - Added ldap_user_create_mode configuration option.
0.1.0 - Init
Note on Updating to Version 0.3 A typo was fixed in the name of a configuration. ldap_bind_db was renamed to ldap_bind_dn. If you update from <0.2 to 0.3, you will have to reset the ldap_bind_dn configuration value. There is a fallback to use the old configuration value, but this will be removed in a future release.
MIT