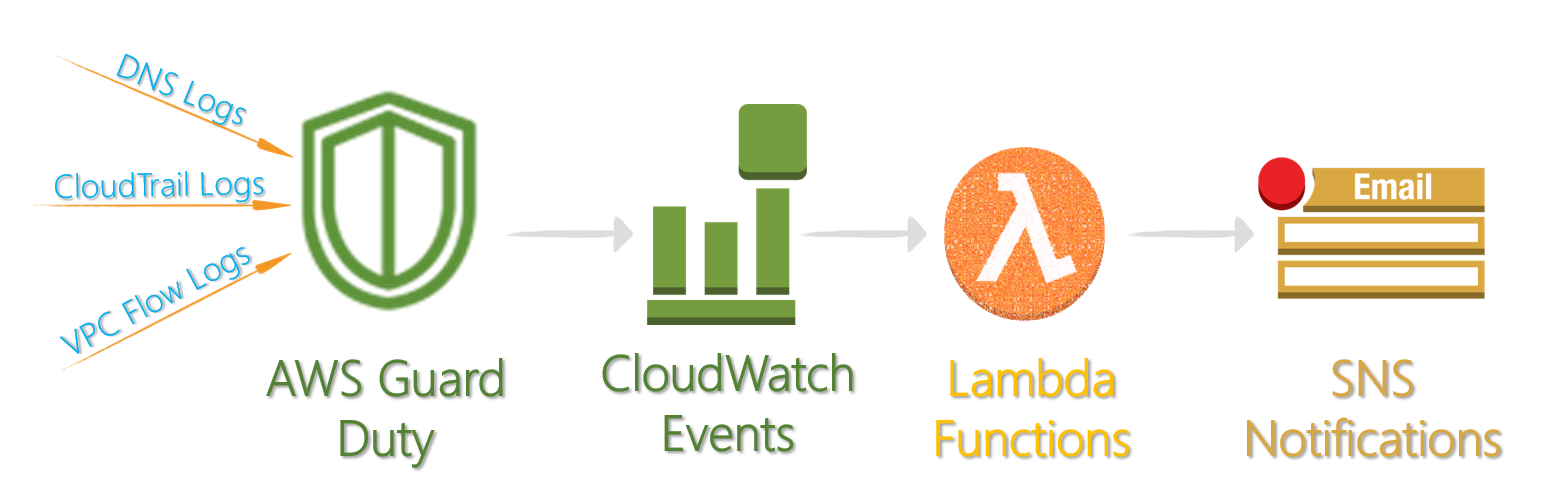
Every GuardDuty finding is assigned a finding ID. For every finding with a unique finding ID, GuardDuty aggregates all subsequent occurrences of a particular finding that take place in six-hour intervals into a single event. GuardDuty then sends a notification about these subsequent occurrences based on this event. We can use this to push the notifications into SNS topic, and getting the security teams to investigate the findings.
This AWS Lambda function will help you to automatically push GuardDuty findings to an SNS topic which can be used by ITSM tools for their workflows.
Follow this article in Youtube
We will need the following pre-requisites to successfully complete this activity,
- A
SNStopic to which our lambda will publish the GuardDuty Findings. Help for setting up SNS Topic<ARN-OF-YOUR-SNS-TOPIC>- We need this to update in the IAM Policy- An email address already subscribed to this topic
- IAM Role - i.e
Lambda Service Role- with two permissions; Help for setting up IAM RoleAWSLambdaBasicExecutionRole- To allow Lambda to log eventsInlinePolicy- To allow Lambda to publish to SNS topic
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "VisualEditor0",
"Effect": "Allow",
"Action": "sns:Publish",
"Resource": "<ARN-OF-YOUR-SNS-TOPIC>"
}
]
}
The python script is written(and tested) in Python 3.6. Remember to choose the same in AWS Lambda Functions.
-
Change the global variables at the top of the script to suit your needs.
globalVars['SNSTopicArn']]- Update the code with your<ARN-OF-YOUR-SNS-TOPIC>; you can also do that using LambdaEnvironment variables
-
Copythe code fromServerless-GuardDuty-Findings-To-SNSin this repo to the lambda function- Consider increasing the lambda run time as needed, the default is
3seconds.
- Consider increasing the lambda run time as needed, the default is
-
Savethe lambda function
Goto the Cloudwatch Dashboard, We are going to use Event Rules
- Choose
Create a new Rule - For
Event Source- ChooseEvent pattern- For
Service, Choose/TypeGuardDuty - For
Event Type, ChooseGuardDuty Finding
- For
- For
Target, ChooseLambda Function- From dropdown select your Lambda Function Name
- In the bottom,
Configure Details - Fill the
Rule Name&Rule Description- Make sure it is Enabled
EnableTrigger byCheckingthe box- Click
Save
Now your lambda function should be triggered when ever there is a GuardDuty Findings
Goto GuardDuty Dashboard. Here we can generate some sample findings from Settings Tab.
Or if you want more sophisticated testing, try out this If you dont have any, considering trying out my Serverless AMI Baker.
We have demonstrated how you can automatically push the findings to SNS Topic.