A demo project explaining the backend authentication using JWT (Json Web Token) authentication using Spring Security & MySQL JPA.
There's support for the following features:
- Conventional email/username based registration with admin support
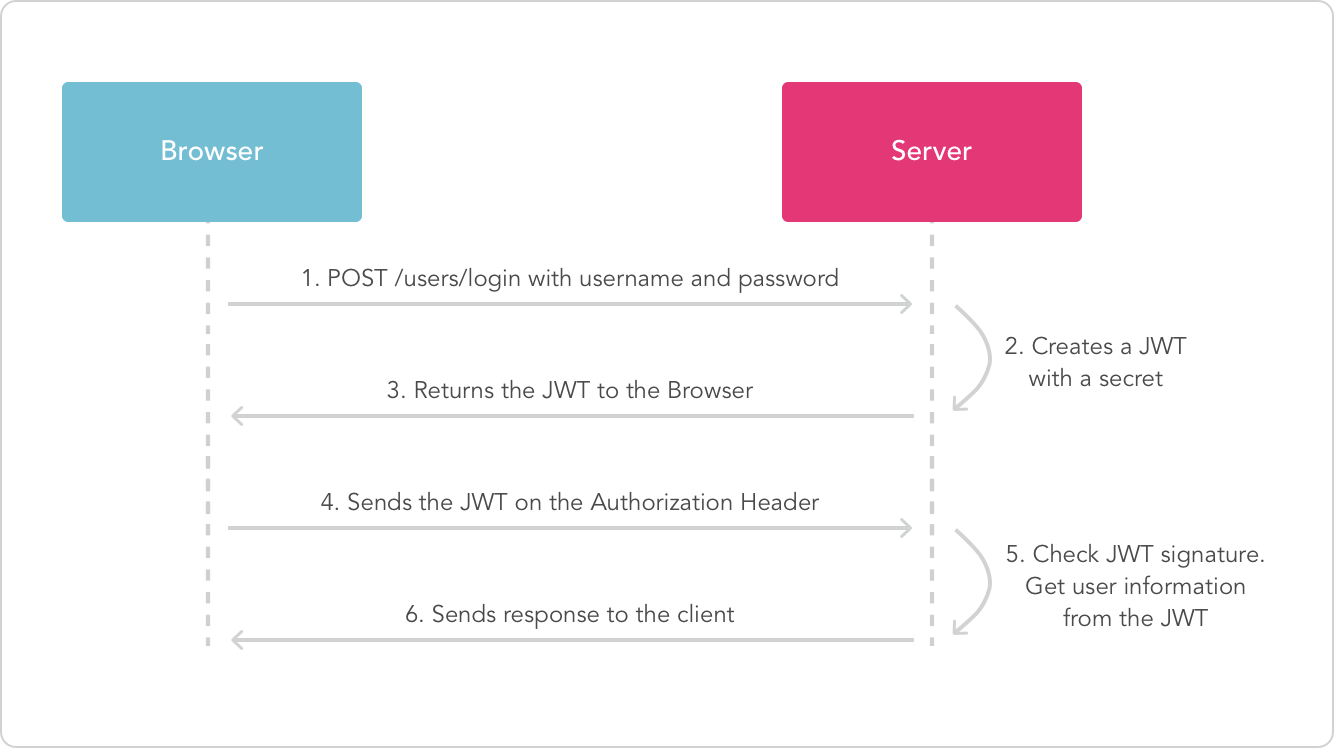
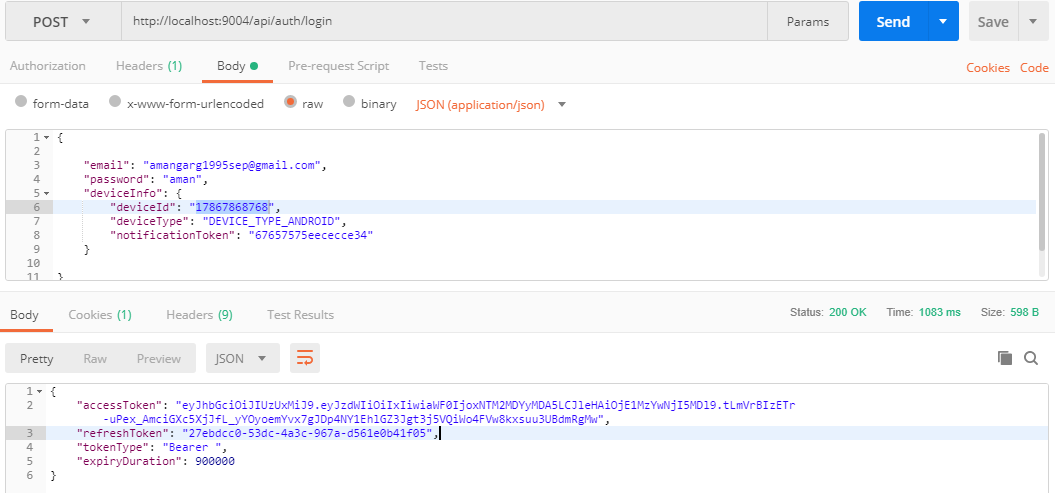
- Conventional Login using Spring Security and generation of JWT token
- Multiple device login and logout support
- In memory store for blacklisting logged out tokens
- Support for expiration bases email verification. Mail is sent upon registration.
- Resend the email confirmation email if old one expires
- Support for password updation once logged in
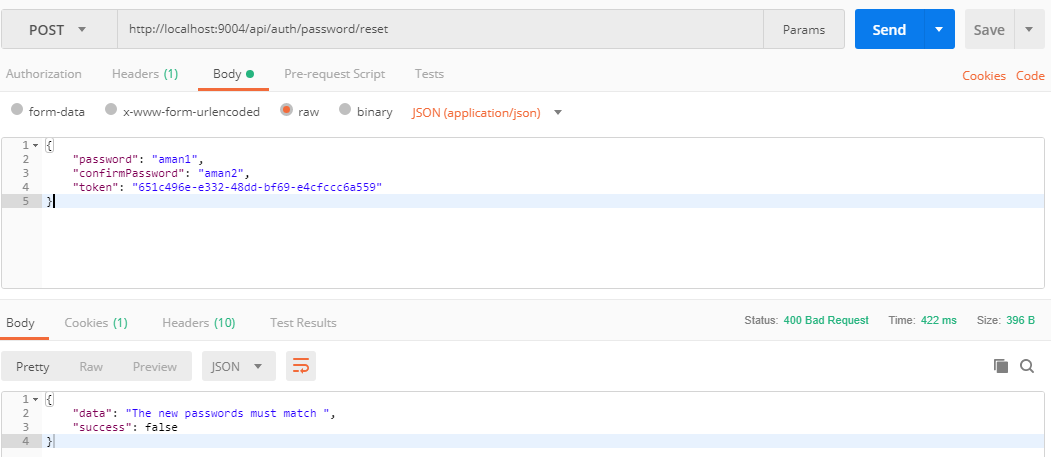
- Support for forgot-password functionality with password reset token sent to mail.
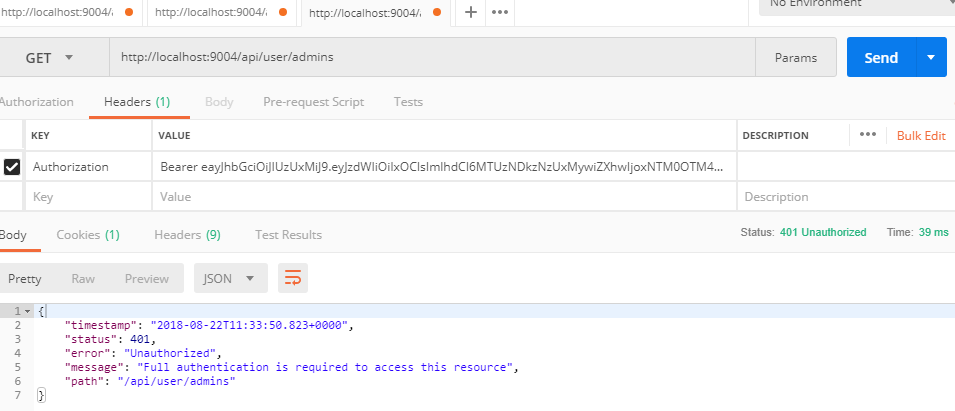
- Supports admin protected urls leveraging Spring security
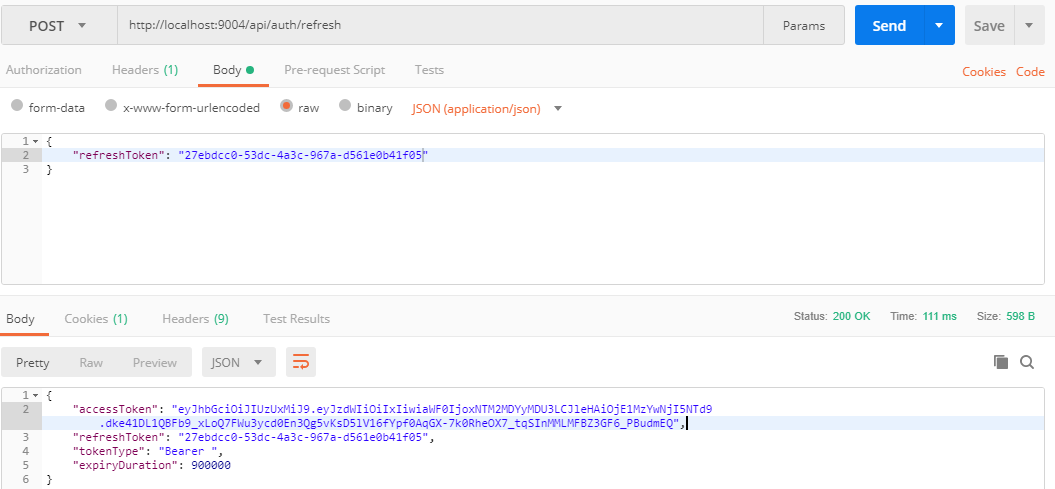
- API to refresh JWT tokens once the temporary JWT expires.
- API to check availability of username/email during registration.
The project has been configured with a basic Swagger docket that exposes the commonly used API's along with the expected params.

JSON Web Tokens are an open, industry standard RFC 7519 method for representing claims securely between two parties.
The app throws custom exceptions wherever necessary which are captured through a controller advice. It then returns the appropriate error response to the caller
- AppException
- BadRequestException
- ResourceAlreadyInUseException
- ResourceNotFoundException
- UserLoginException
- UserRegistrationException
- MethodArgumentNotValidException
- UserLogoutException
- TokenRefreshException
- UpdatePasswordException
- PasswordResetException
- PasswordResetLinkException
Moreover, entities are validated using JSR-303 Validation constraints.
-
Clone the application
git clone https://github.com/isopropylcyanide/Jwt-Spring-Security-JPA.git cd AuthApp -
Create a MySQL database
create database login_db
-
Change MySQL username and password as per your MySQL installation
-
open
src/main/resources/application.propertiesfile. -
change
spring.datasource.usernameandspring.datasource.passwordproperties as per your mysql installation -
open
src/main/resources/mail.propertiesfile. -
change
spring.mail.usernameandspring.mail.passwordproperties as per your mail installation
-
-
Run the app
You can run the spring boot app by typing the following operating system specific command -
For UNIX/Linux based operating systems,
./mvnw spring-boot:run
For Windows based operating systems,
mvnw.cmd spring-boot:run
The server will start on port 9004. Token default expiration is 600000ms i.e 10 minutes.
-
Add the default Roles
The spring boot app uses role based authorization powered by spring security. Please execute the following sql queries in the database to insert the
USERandADMINroles.INSERT INTO ROLE (ROLE_NAME) VALUES ('ROLE_USER'); INSERT INTO ROLE (ROLE_NAME) VALUES ('ROLE_ADMIN');
Any new user who signs up to the app is assigned the
ROLE_USERby default.
- Please fork the project and adapt it to your use case.
- Submit a pull request.
- Registering a user
- Logging in a valid user
- Logging in an invalid user
- Using the token in request header & accessing resource
- Accessing admin resource with invalid permissions/token
- Logging out the user device
- Resetting the password
- Refreshing the authentication token
- Confirming the user email verification token