-
Notifications
You must be signed in to change notification settings - Fork 0
Knowledge Base
UPDATED: Important dates for timestamping service changes 2023/24
- July 2023 - new TSA servive endpoints available in TEST environment - EXECUTED
- 07.11.2023 - TEST endpoint switch to new PKI chain (See Figure 3) - EXECUTED
- 08.11.2023 - new TSA service production endpoints available (See Figure 4) - EXECUTED
- 24.01.2024 @14:00 EET - PRODUCTION endpoint tsa.sk.ee switch to new PKI chain (See Figure 5) - EXECUTED
1. What are the main differences between current and future setup?
Current timestamping service available for production (tsa.sk.ee) and test (tsa.demo.sk.ee) uses RSA 2048 key size and timestamping certificate issued as follows:
TEST: TEST of EE Certification Centre Root CA → DEMO SK TIMESTAMPING AUTHORITY 2020
PRODUCTION: EE Certification Centre Root CA → SK TIMESTAMPING AUTHORITY 2023. See Figure 1 for current production setup.
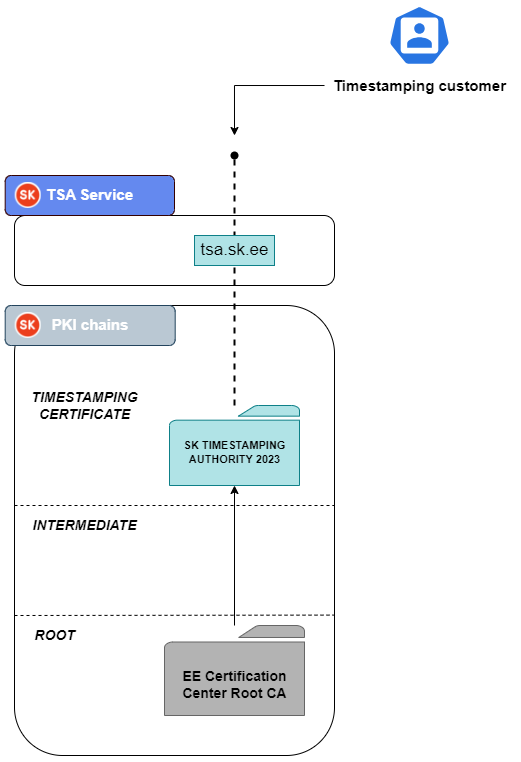
Figure 1: Current production setup of timestamping service
Firstly, new timestamping service certificates will be issued under new PKI hierarchy. Before certificate was issued directly under root, now there will be intermediate certificate under which timestamping certificate is being issued.
Secondly, timestamping service certificate will have ECC (Elliptic Curve Cryptography) 256 key pair and also RSA 4096-bit key length.
Thirdly, there will be two new timestamping service endpoints available in addition to the existing one.
New PKI hierarchy together with new service endpoints are illustrated on Figure 2/3 for test environment and on Figure 4/5 for production setup.

Figure 2: Current setup for test environment (valid until 07.11.2023)

Figure 3: Setup for test environment (valid from 07.11.2023)

Figure 4: New setup for production environment for period 08.11.2023 - 23.01.2024

Figure 5: Production environment setup starting 24.01.2024 14:00
2. How the change could be tested? In TEST timestamping service, there are two brand new endpoints available in addition to existing one, by following:
EXISTING:
- http://tsa.demo.sk.ee/tsa - uses 2048 bit RSA key, certificate issued under test root certificate named CN=TEST of EE Certification Centre Root CA. Will start using new PKI hierarchy (certificate with ECC 256-bit integer) from 07.11.2023
NEW:
- http://tsa.demo.sk.ee/tsaecc - uses ECC 256 bit integer key, certificate is issued under intermediate CA named CN=TEST of SK TSA CA 2023E
- http://tsa.demo.sk.ee/tsarsa - uses 4096 bit RSA key, certificate is issued under intermediate CA named CN=TEST of SK TSA CA 2023R
Please check Figure 2 to see picture of test environment setup. The same setup will be also in production see Figure 3! All new test PKI chain certificates can be found from SK repository under tab named "Test certificates" here
3. What are the new production service endpoints and where could new certificates be downloaded?
New TSA service endpoints for production:
- http://tsa.sk.ee/ecc
- http://tsa.sk.ee/rsa
(all endpoints available also in HTTPS)
New PKI chain certificates can be found in SK repository
ROOT certificates:
Issuing CA certificates:
Timestamping Unit certificates:
4. When will the change come into effect?
We have already initiated changes in timestamping TEST environment so that you can already start testing. We will provide exact and detailed timeline during September 2023 about changes planned for production environment.
Update: New timestamping service endpoints will be available in production starting 08.11.2023
5. Who will be affected by this change?
All e-services, applications and information systems using directly or indirectly SK timestamping service, but not limited to:
- X-road users (security server owners) - new timestamping service endpoints will be configured in X-road ecosystem by Estonian Information System Authority (RIA). Further changes regards X-road will be done/guided by RIA.
- signing solution providers
- solutions which use custom trust store for certificates instead of EU Trusted List
6. What are the key aspects to pinpoint, to keep everything working and be ready on time?
- make sure that new PKI hierarchy certificates in your information system are supported/trusted
- test new endpoints as soon as possible to adopt with new signing algorithms.
- make changes, if necessary.
7. What will happen if you do nothing?
It is important to note that production endpoint tsa.sk.ee will stay available but will start using new PKI hierarchy and certificate with ECC 256-bit integer from January 2024. Your solutions might stop working if they are not compatible with new setup.
We recommend you to test your services in our public test environment and verify that your services are ready to support the changes ahead!
8. Why are all these changes necessary?
Transition to new PKI hierarchy is needed to replace the current EE Certification Centre Root CA chain what will be expired by end of 2030. Moving to new PKI hierarchy and using more secure key lenghts add more security and helps to preserve the integrity of timestamps.
9. What will happen with current Timestamping PKI hierarchy (EE Certification Centre Root CA), will it fade away? YES! It will happen in January 2024, when timestamping certificate under new PKI TSA will be used by default under tsa.sk.ee endpoint. We will provide you with more detailed information during September 2023 about exact change timeline for production environment.
Update: tsa.sk.ee will be switched on new PKI chain 24.01.2024. See Figure 5 above.
10. What about new timestamping service being in Trusted list?
Production timestamping certificates (ECC and RSA) added in the EE Trusted List (EU Trusted List)
Test certificates are added into test Trusted List https://open-eid.github.io/test-TL/ managed by RIA (Estonian Information System Authority).