An alpine-based docker image with shadowsocks + kcptun, brook and shadowsocksr for crossing the GFW.
- 1、Prepare a cloud server with CentOS7 for building proxy services.(vultr, do or bwh...)
- 2、Install Docker
yum -y update
yum install -y yum-utils device-mapper-persistent-data lvm2
yum-config-manager --add-repo https://download.docker.com/linux/centos/docker-ce.repo
yum -y install docker-ce
systemctl start docker
systemctl enable docker - 3、Pull this image
docker pull zhoubowen123/shadowsocks-kcptun - 4、Create a container
docker run --privileged --restart=always -tid -p 10000:10000 -p 10001:10001 -p 10002:10002/tcp -p 10002:10002/udp -p 4000:4000/udp -p 4000:4000/tcp zhoubowen123/shadowsocks-kcptun /sbin/init
docker run --privileged --restart=always -tid -p 10002:10002/tcp -p 10002:10002/udp -p 4000:4000/udp -p 4000:4000/tcp zhoubowen123/shadowsocks-kcptun /sbin/init - 5、Emmmmm...
Now the server is finished. You can access Google through ss, ssr or brook client, here are parameters for these clients.
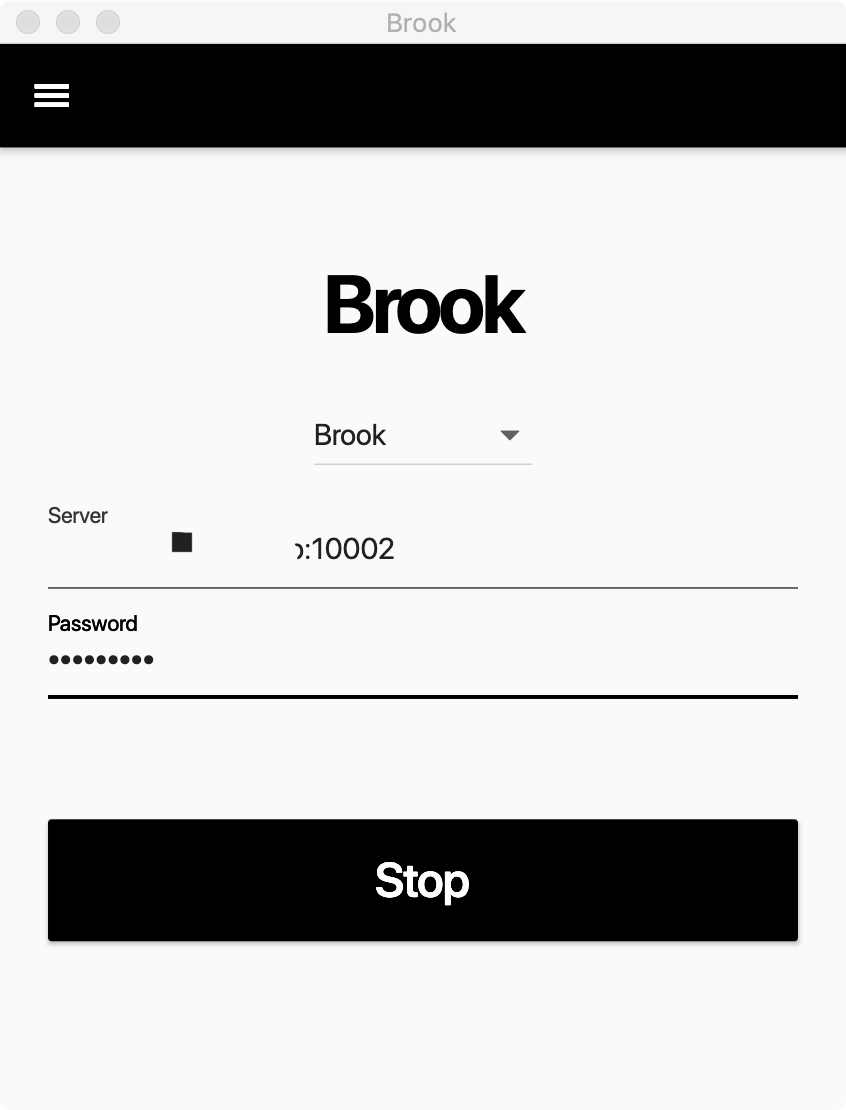
- Brook ip:
your server ip - Brook port:
10002 - Brook passwd:
qazwsxedc
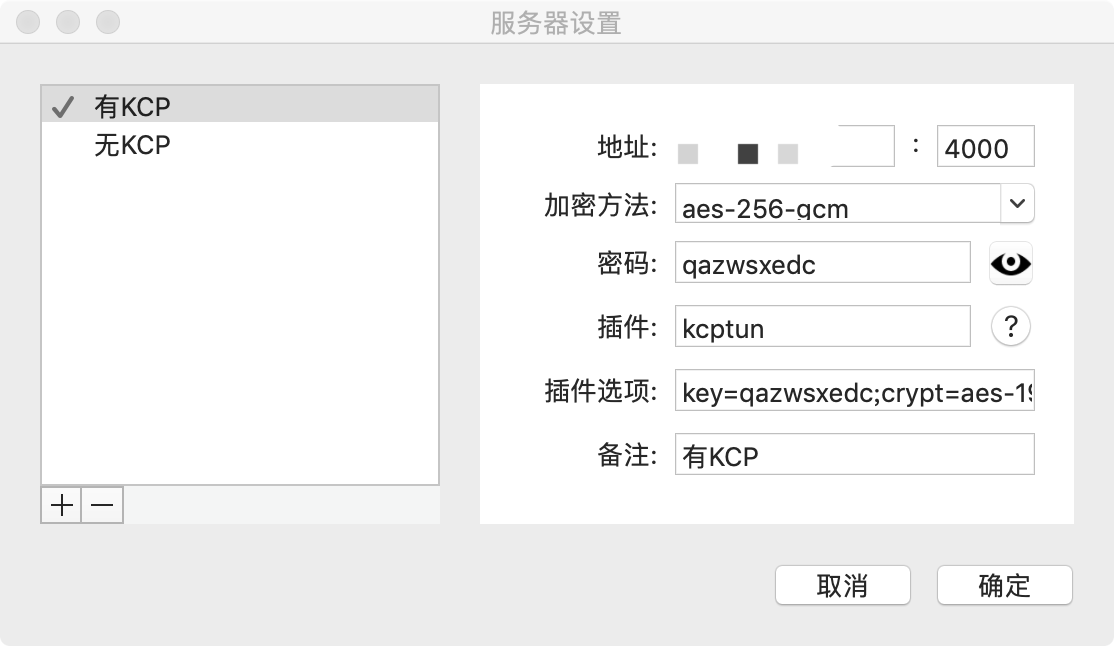
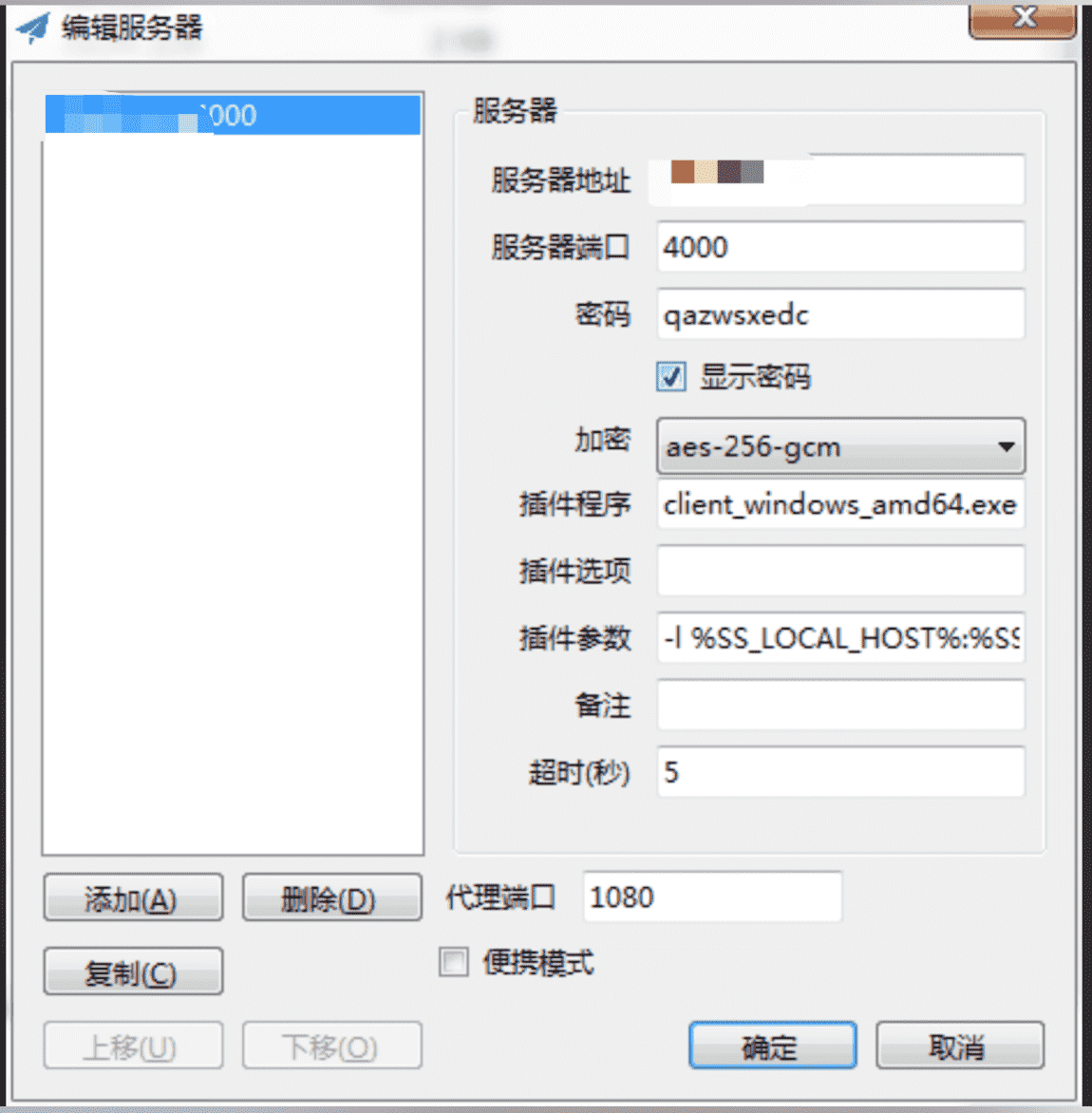
- kcptun port:
4000 - kcptun passwd:
qazwsxedc - kcptun encrypt:
aes-192 - kcptun mode:
fast2 - kcptun autoexpire:
60
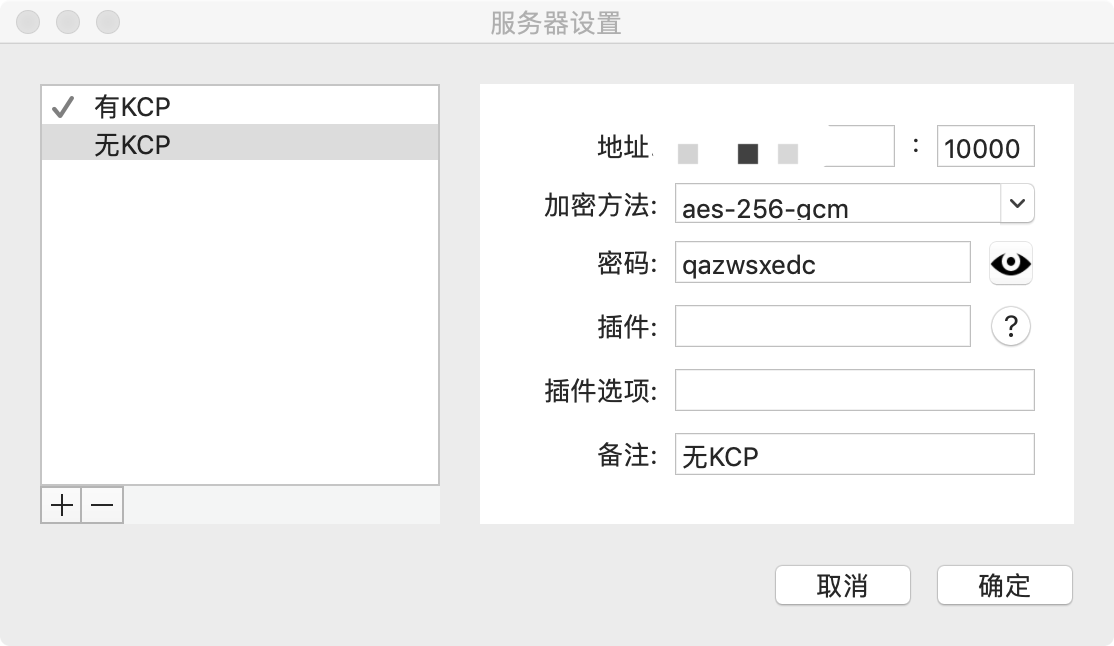
- Ss ip:
your server ip - Ss port:
10000 - Ss passwd:
qazwsxedc - Ss encrypt:
aes-256-gcm
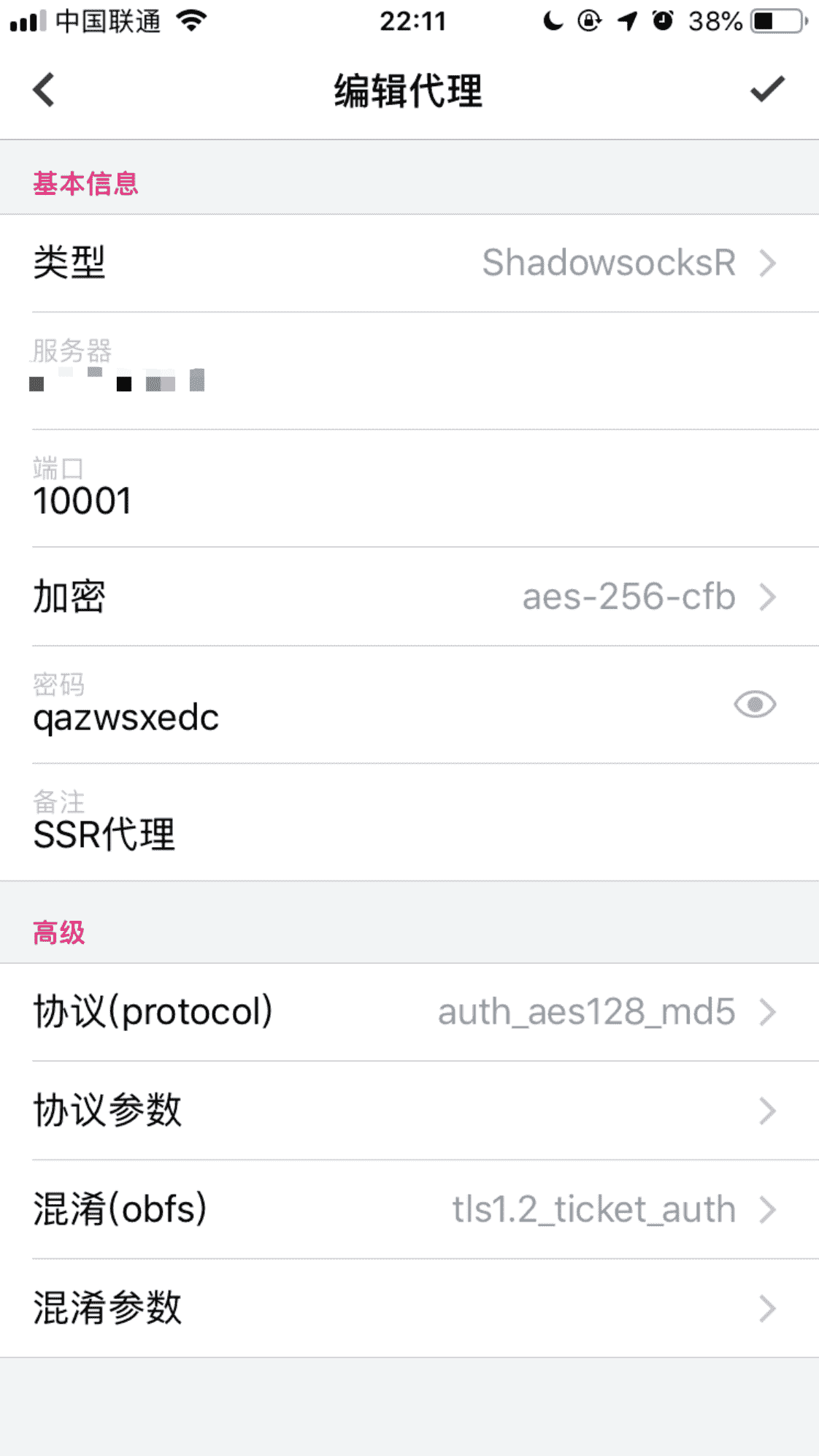
- Ssr ip:
your server ip - Ssr port:
10001 - Ssr passwd:
qazwsxedc - Ssr encrypt:
aes-256-cfb - Ssr protocol:
auth_aes128_md5 - Ssr obfs:
tls1.2_ticket_auth
to be continued ...
kcptun plugin option (for mac):
key=qazwsxedc;crypt=aes-192;mode=fast2;autoexpire=60
kcptun plugin option (for windows):
-l %SS_LOCAL_HOST%:%SS_LOCAL_PORT% -r %SS_REMOTE_HOST%:%SS_REMOTE_PORT% --key qazwsxedc --crypt aes-192 --mode fast2 --autoexpire 60