-
Notifications
You must be signed in to change notification settings - Fork 7
NAT Stateful
Stateful (also called dynamic) NAT maps many private IP addresses to public address(es).
To configure stateful NAT, use the tc iproute2 tool, and the tc-ct action.
For dynamic NAT entry offloading, combine the tc-ct action with the flower filter rule and ingress qdisc.
For more information on stateful NAT, see the tc-flower and tc-ct man pages.
NOTE: The stateful NAT feature requires Linux kernel 5.8.9 and above.
This example covers the basic use case (many to one, with one private Switchdev port) of stateful NAT configuration using a TC connection tracking subsystem. The following image shows the basic configuration setup:
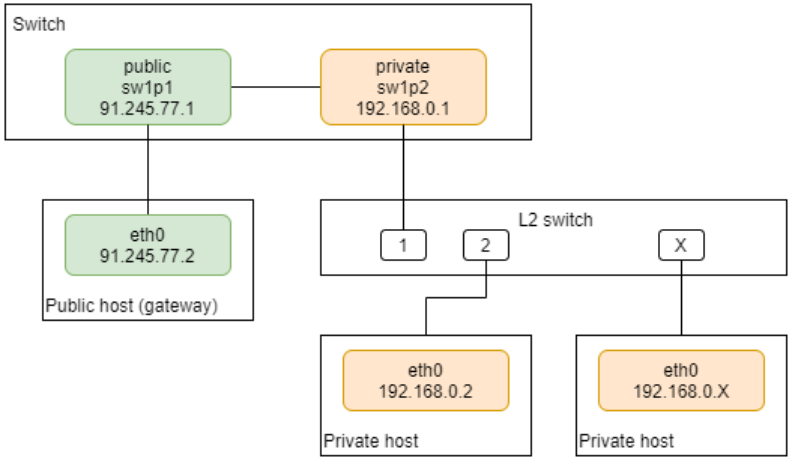
NOTE: the same scenario also covers the case of only one private host.
The following examples show various configuration options.
Configuration of a private host connected to the switch device (in this case on one private):
# private host: IP/default gateway
ip addr add dev eth0 192.168.0.2/24
ip route add default via 192.168.0.1
Configuration of public host connected to the switch device:
# public host: IP
ip addr add dev eth0 91.245.77.2/24
IP configuration on the switch:
# switch: private/public interface IP
ip addr add dev sw1p2 192.168.0.1/24
ip addr add dev sw1p1 91.245.77.1/24
Adding a default gateway on the switch to route packets via public interface.
ip route add default via 91.245.77.1
Configuration of connection tracking on private port:
tc qdisc add dev sw1p2 clsact
tc filter add dev sw1p2 ingress proto ip pref 2 flower ct_state -trk \
action ct
Configure NAT connection tracking on public port:
tc qdisc add dev sw1p1 clsact
tc filter add dev sw1p1 egress prio 10 proto ip flower \
action ct commit nat src addr 91.245.77.1 pipe action pass
tc filter add dev sw1p1 ingress prio 5 proto ip flower \
action ct nat pipe action pass
NOTE: Since the NAT configuration uses regular ACL rules, it takes resources from regular ACL memory.
NOTE: Egress CT flower filter match on a public port should be the same as CT flower filter on a private port. If a CT rule exists on multiple private port, those flower matches should be reflected on egress public port.
To skip NAT for packets that are designated as a private subnet or as hosts, you need to install additional hardware offload rules (skip_sw flower option) on private ports. For example, a rule that matches a private subnet with a higher priority should be installed with the action “do nothing”, on each of the private ports.
tc filter add dev sw1p2 protocol ip ingress \
flower skip_sw ip_proto tcp dst_ip 192.168.0.1/24 action pass
NOTE: The last added rule has a higher priority, so the priority can be skipped in the rule. For more information, see ACL.
Network Configurations
- Switch Port
- Layer 2
- Layer 3
- Dynamic SCT
- Quality of Service (QoS)
- Access Control Lists (ACL)
- Network Address Translation (NAT)
- Debugging Tools and and Methods
- Resources and Releases
- Marvell® Switchdev Slim (Single-CPU) mode guide