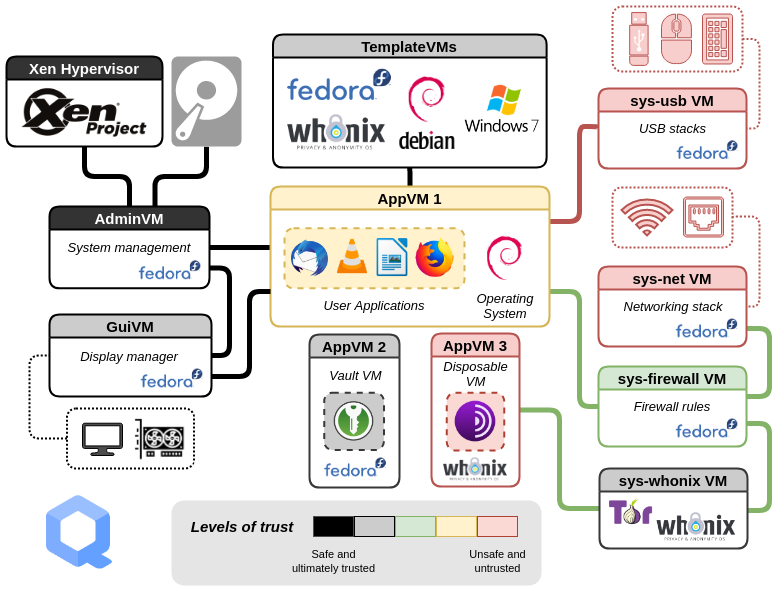
A reasonably secure base setup for offensive security operations and research.
This set up is based on Qubes OS and heavily focuses on isolation and compartmentalization. It will give you a solid base to work from using some of Qubes most powerfull features.
I want to give massive credits to the exceptional Qubes OS project, for making this OS and all the documentation behind it.
The above images are from the Qubes project and will give you an idea of how a set up could look.
- Base setup
- Set up i3
- Set up Yubikey
- Minimal pass vault
- Split-GPG
- Split-SSH
- VPN Qube
- Security considerations
- Hypervisor security considerations
- USB security considerations
- Security considerations of updating systems
- Security considerations of passwords, GPG-keys and SSH-keys
- Clipboard security considerations
- Storage security considerations
- Security considerations sharing files between vms
- Network security considerations
Use disposable vm's for as much as possible such as browsing the web and handle untrusted files.
While this will give you the base setup, you will then need to tailor it to your needs including creating vm's such as Windows development machines, secure communication vm's and Kali linux boxes.
I have also tired so summerize the most important security considerations that are behind the design of the set-up.