-
Notifications
You must be signed in to change notification settings - Fork 567
[User Guide] Connectivity Resources
The module provides an option to enable deployment of network topology and connectivity resources from the conceptual architecture for Azure landing zones into the current subscription context. It also ensures that the specified subscription is placed in the right management group.
This capability enables deployment of multiple hub networks based on any combination of traditional Azure networking topology (hub and spoke), and Virtual WAN network topology (Microsoft-managed).
The module can also create and link DDoS Protection Standard to Virtual Networks, and manage centralized public and private DNS zones.
NOTE: The module currently only configures the hub network(s), and other recommended resources for the
connectivitySubscription. To ensure the right balance of managing resources via Terraform vs. Azure Policy, we are still working on how best to handle the creation and peering of spoke Virtual Networks. Improving this story is on our backlog for development.
The module can optionally deploy one or more hub networks based on the traditional Azure networking topology (hub and spoke).
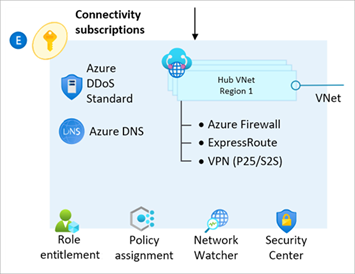
NOTE: The module currently configures only the networking hub and dependent resources for the connectivity subscription. Although there's an option to enable outbound virtual network peering from hub to spoke, users still need to initiate peering from spoke to hub. This is due to limitations in how the AzureRM provider targets a specific subscription for deployment.
When you deploy resources based on a traditional Azure networking topology (hub and spoke), the module deploys and manages the following resource types (depending on configuration):
| Resource | Azure resource type | Terraform resource type |
|---|---|---|
| Resource groups | Microsoft.Resources/resourceGroups |
azurerm_resource_group |
| Virtual networks | Microsoft.Network/virtualNetworks |
azurerm_virtual_network |
| Subnets | Microsoft.Network/virtualNetworks/subnets |
azurerm_subnet |
| Virtual network gateways | Microsoft.Network/virtualNetworkGateways |
azurerm_virtual_network_gateway |
| Azure firewalls | Microsoft.Network/azureFirewalls |
azurerm_firewall |
| Public IP addresses | Microsoft.Network/publicIPAddresses |
azurerm_public_ip |
| Virtual network peerings | Microsoft.Network/virtualNetworks/virtualNetworkPeerings |
azurerm_virtual_network_peering |
For more information about how to use this capability, see the Deploy Connectivity Resources wiki page.
The module can optionally deploy one or more hub networks based on the Virtual WAN network topology (Microsoft-managed).
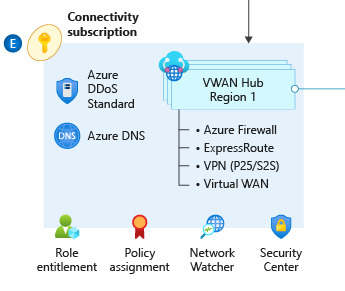
NOTE: Due to the different capabilities of Virtual WAN network resources over traditional, peering for Virtual WAN spokes is bi-directional when using this capability.
When you deploy resources based on a Virtual WAN network topology (Microsoft-managed), the module deploys and manages the following resource types (depending on configuration):
| Resource | Azure resource type | Terraform resource type |
|---|---|---|
| Resource Groups | Microsoft.Resources/resourceGroups |
azurerm_resource_group |
| Virtual WANs | Microsoft.Network/virtualWans |
azurerm_virtual_wan |
| Virtual Hubs | Microsoft.Network/virtualHubs |
azurerm_virtual_hub |
| Express Route Gateways | Microsoft.Network/expressRouteGateways |
azurerm_express_route_gateway |
| VPN Gateways | Microsoft.Network/vpnGateways |
azurerm_vpn_gateway |
| Azure Firewalls | Microsoft.Network/azureFirewalls |
azurerm_firewall |
| Azure Firewall Policies | Microsoft.Network/firewallPolicies |
azurerm_firewall_policy |
| Virtual Hub Connections | Microsoft.Network/virtualHubs/hubVirtualNetworkConnections |
azurerm_virtual_hub_connection |
For more information about how to use this capability, see the Deploy Virtual WAN Resources With Custom Settings wiki page.
The module can optionally deploy DDoS Network Protection, and link Virtual Networks to the plan if needed.
NOTE: Due to platform limitations, DDoS protection plans can only be enabled for traditional virtual networks. Virtual Hub support is not currently available.
IMPORTANT: The Azure landing zones guidance recommends enabling DDoS Network Protection to increase protection of your Azure platform. To prevent unexpected costs in non-production and MVP deployments, this capability is disabled in the Azure landing zones Terraform module due to the cost associated with this resource.
For production environments, we strongly recommend enabling this capability.
When you enable deployment of deployment of DDoS protection plan resources, the module deploys and manages the following resource types (depending on configuration):
| Resource | Azure resource type | Terraform resource type |
|---|---|---|
| Resource groups | Microsoft.Resources/resourceGroups |
azurerm_resource_group |
| DDoS protection plans | Microsoft.Network/ddosProtectionPlans |
azurerm_network_ddos_protection_plan |
The module can optionally deploy Private DNS zones to support Private Endpoints and link them to hub and/or spoke Virtual Networks. User-specified public and private DNS zones can also be deployed and linked as needed.
When you enable deployment of deployment of DNS resources, the module deploys and manages the following resource types (depending on configuration):
| Resource | Azure resource type | Terraform resource type |
|---|---|---|
| Resource Groups | Microsoft.Resources/resourceGroups |
azurerm_resource_group |
| DNS Zones | Microsoft.Network/dnsZones |
azurerm_dns_zone |
| Private DNS Zones | Microsoft.Network/privateDnsZones |
azurerm_private_dns_zone |
| Private DNS Zone Virtual Network Link | Microsoft.Network/privatednszones/virtualnetworklinks |
azurerm_private_dns_zone_virtual_network_link |
Please refer to the following for examples showing how to use this capability:
This wiki is being actively developed
If you discover any documentation bugs or would like to request new content, please raise them as an issue or feel free to contribute to the wiki via a pull request. The wiki docs are located in the repository in the docs/wiki/ folder.
- Home
- User guide
- Video guides
-
Examples
- Level 100
- Level 200
-
Level 300
- Deploy multi region networking with custom settings (Hub and Spoke)
- Deploy multi region networking with custom settings (Virtual WAN)
- Deploy with Zero Trust network principles (Hub and Spoke)
- Deploy identity resources with custom settings
- Deploy management resources with custom settings
- Expand built-in archetype definitions
- Create custom policies, initiatives and assignments
- Override module role assignments
- Control policy enforcement mode
- Policy assignments with user assigned managed identities
- Level 400
- Frequently Asked Questions
- Troubleshooting
- Contributing