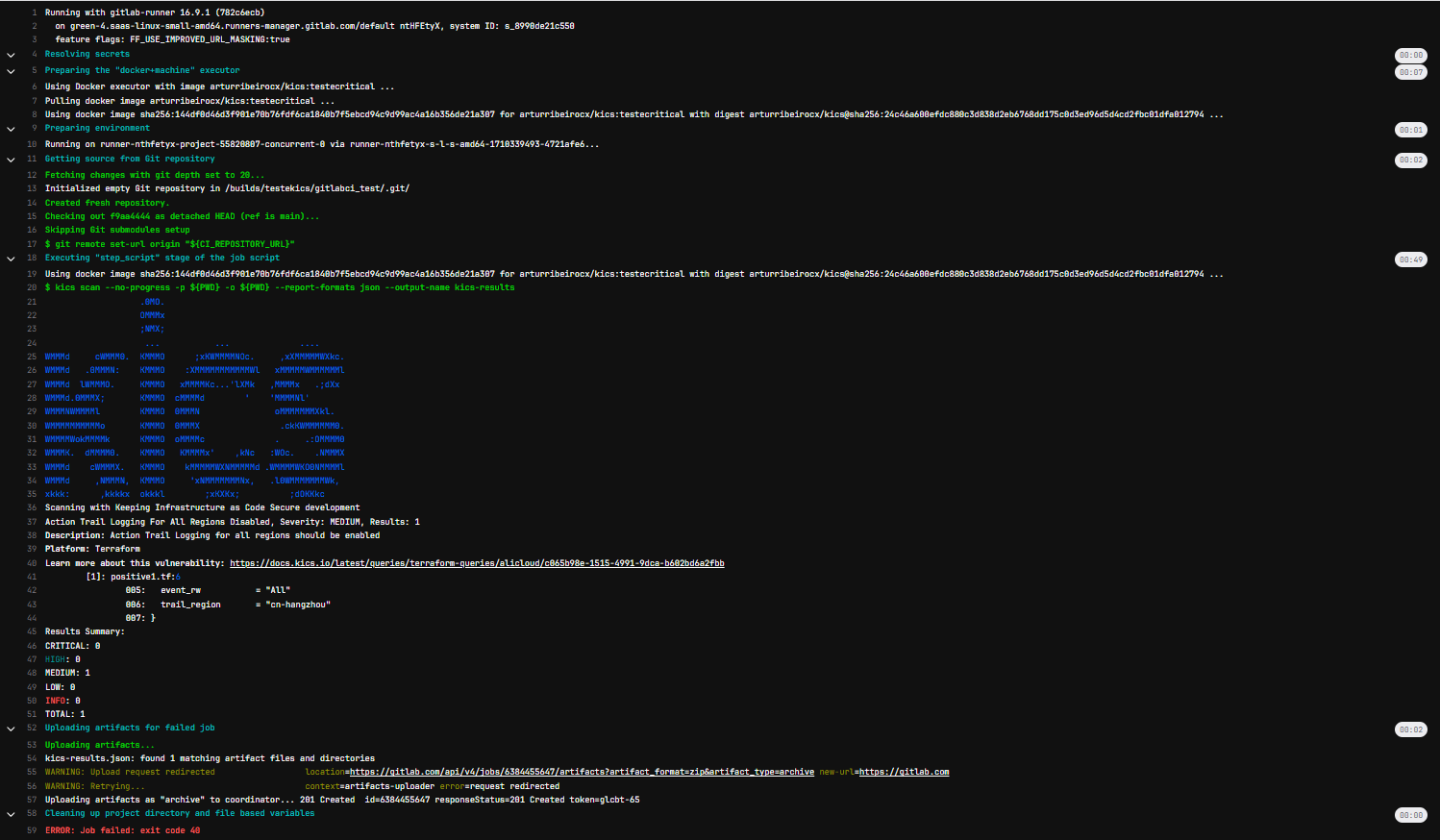
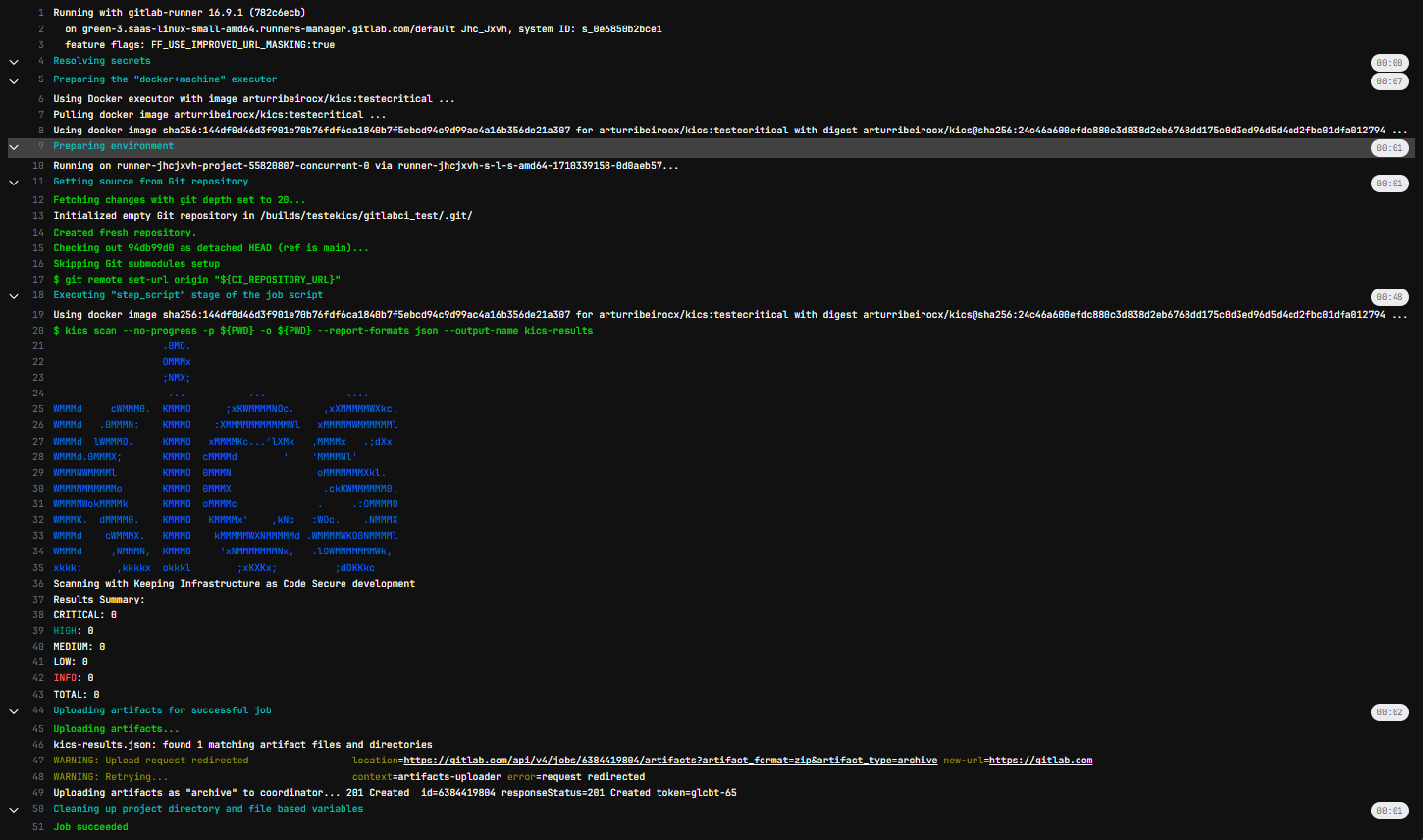
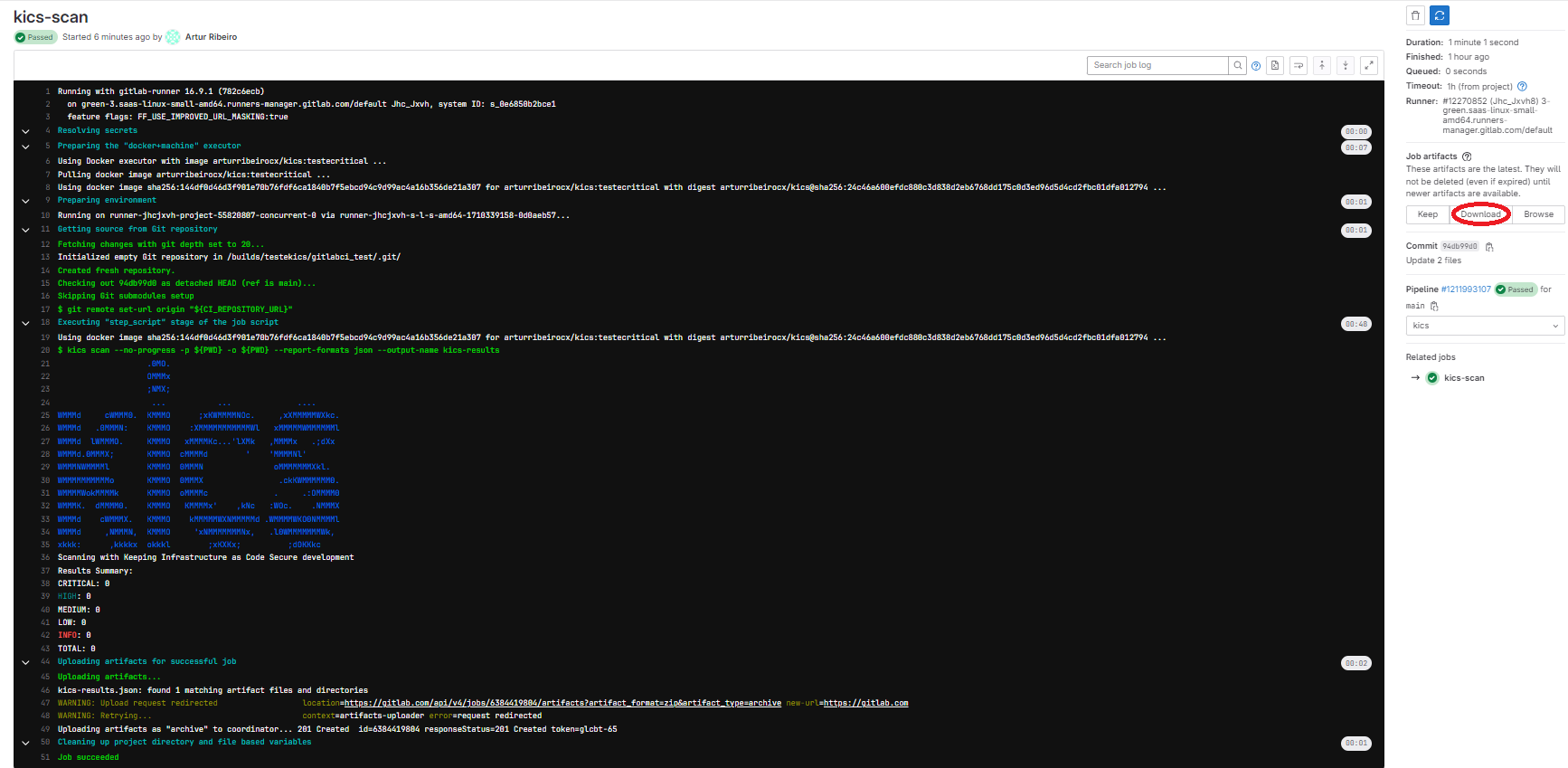
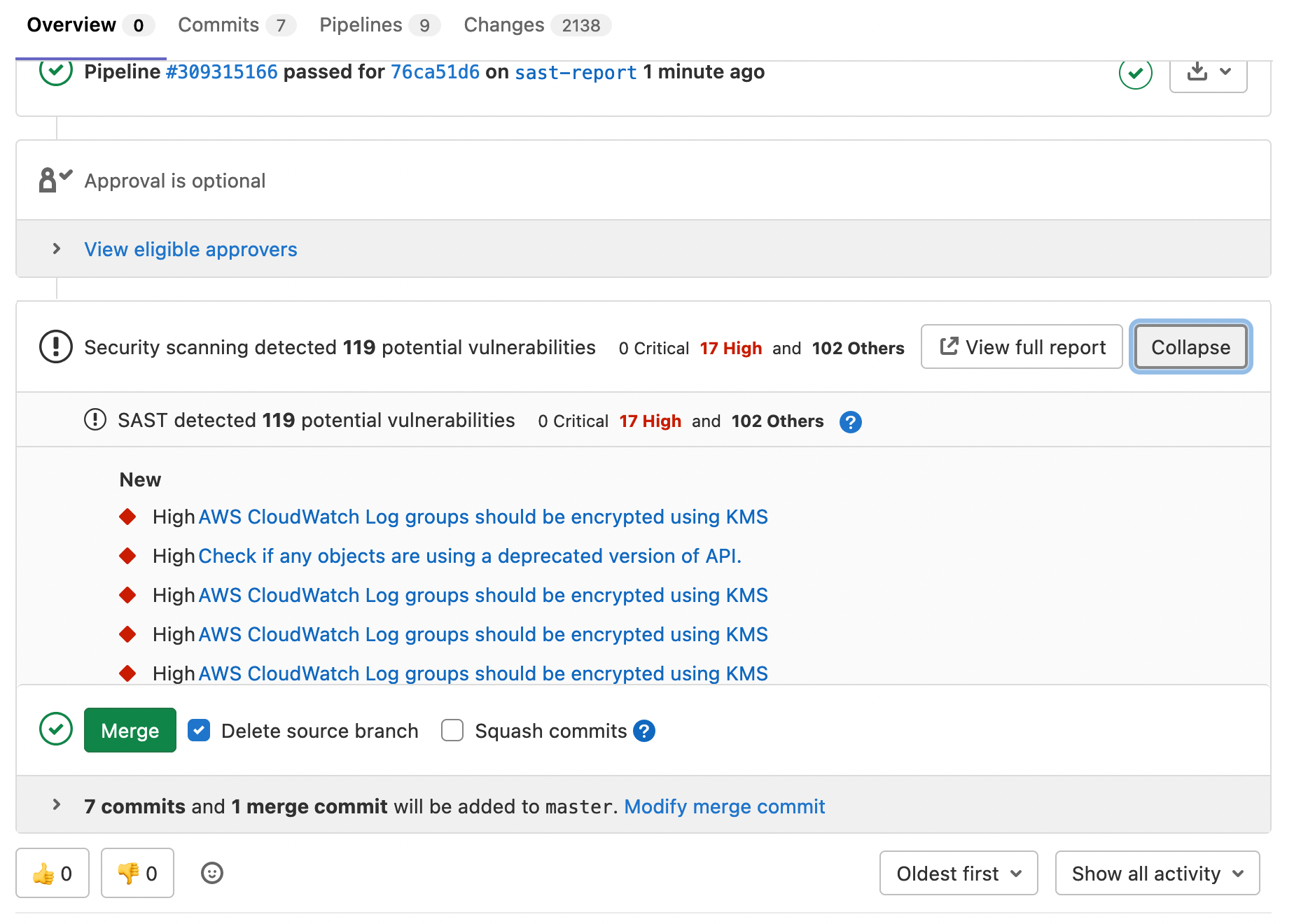
You can integrate KICS into your GitLab CI/CD pipelines.
This provides you the ability to run KICS scans in your GitLab repositories and streamline vulnerabilities and misconfiguration checks to your infrastructure as code (IaC).
image:
name: checkmarx/kics:latest
entrypoint: [""]
stages:
- kics
kics-scan:
stage: kics
script:
- kics scan --no-progress -p ${PWD} -o ${PWD} --report-formats json --output-name kics-results
artifacts:
name: kics-results.json
paths:
- kics-results.json
when: alwaysWhen your pipeline executes, it will run this job. If KICS finds any issues, it will fail the build.
image:
name: checkmarx/kics:latest
entrypoint: [""]
stages:
- kics
kics-scan:
stage: kics
script:
- kics scan -p ${PWD} --ignore-on-exit all --report-formats glsast -o ${PWD} --output-name kics-results
artifacts:
reports:
sast: gl-sast-kics-results.json
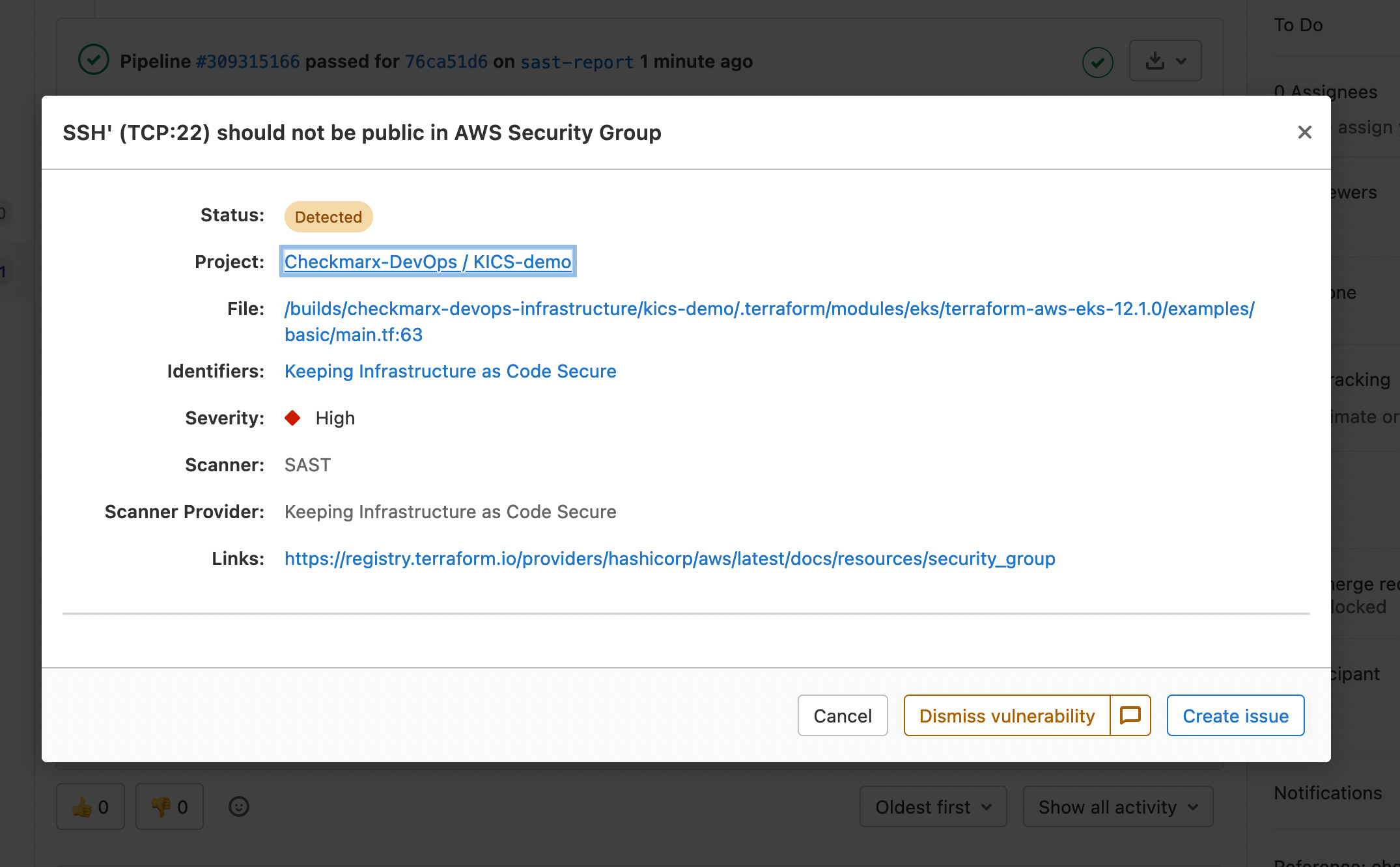
when: always📝 This feature requires Gitlab Ultimate.
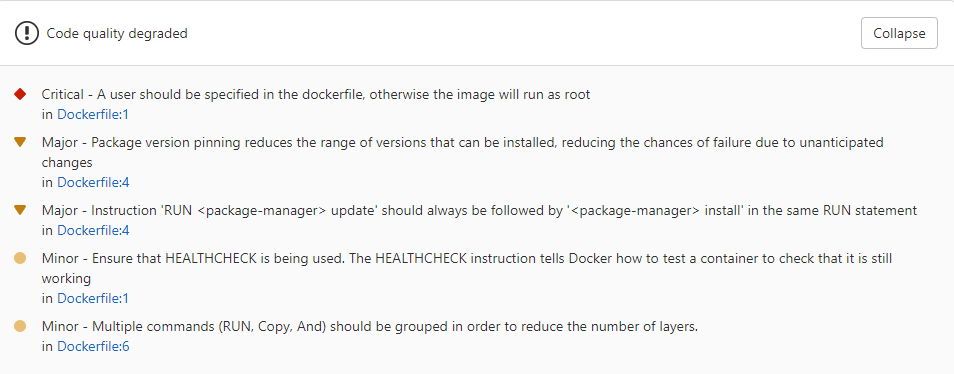
It is possible to get code quality report with Kics scan, see the example:
image:
name: checkmarx/kics:latest
entrypoint: [""]
stages:
- test
code_quality:
stage: test
script:
- kics scan --no-progress -p ${PWD} -o ${PWD} --report-formats codeclimate --output-name codeclimate-result
artifacts:
paths:
- codeclimate-result.json
reports:
codequality: codeclimate-result.json