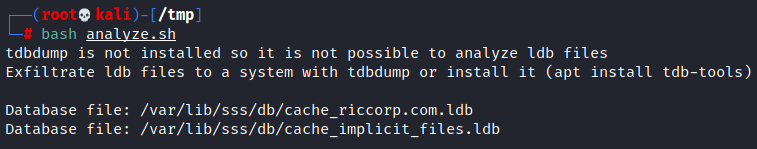
Using this bash script it is possible to extract Active Directory accounts hashes when credential caching is enabled in SSSD.
bash analyze.sh [$path]
Without input arguments it takes the SSSD default path "/var/lib/sss/db/" but you can use a different one. If tdbdump is not installed it just lists the ldb files which contain the hashes, you can install it ("apt install tdb-tools") or exfiltrate these files:
In a system with tdbdump installed the script extracts the cached accounts and hashes, dumping the results to the file "hashes.txt"
The hashes can then be cracked using Hashcat or John the Ripper:
john hashes.txt --format=sha512crypt
I created the script after reading this presentation by Tim (Wadhwa-)Brown: Where 2 worlds collide - Bringing Mimikatz et al to UNIX