-
Notifications
You must be signed in to change notification settings - Fork 0
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Revisit Authentication Common Sense as a Web developer #175
Comments
Password Authentication
|
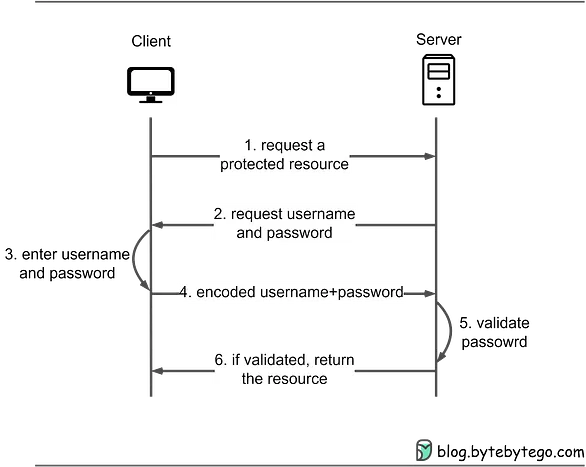
HTTP Basic AuthenticationThe flow of HTTP Basic Authentication
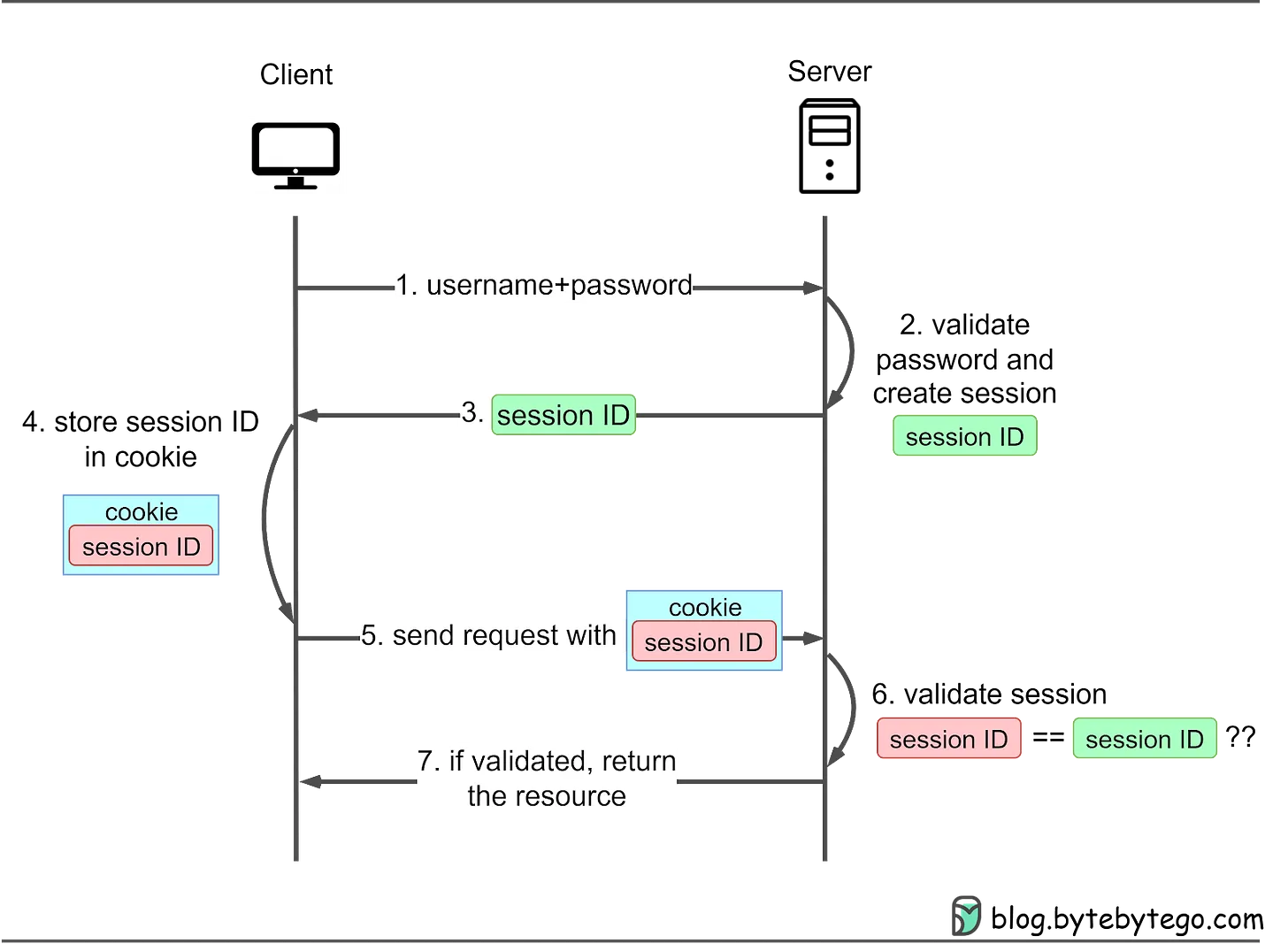
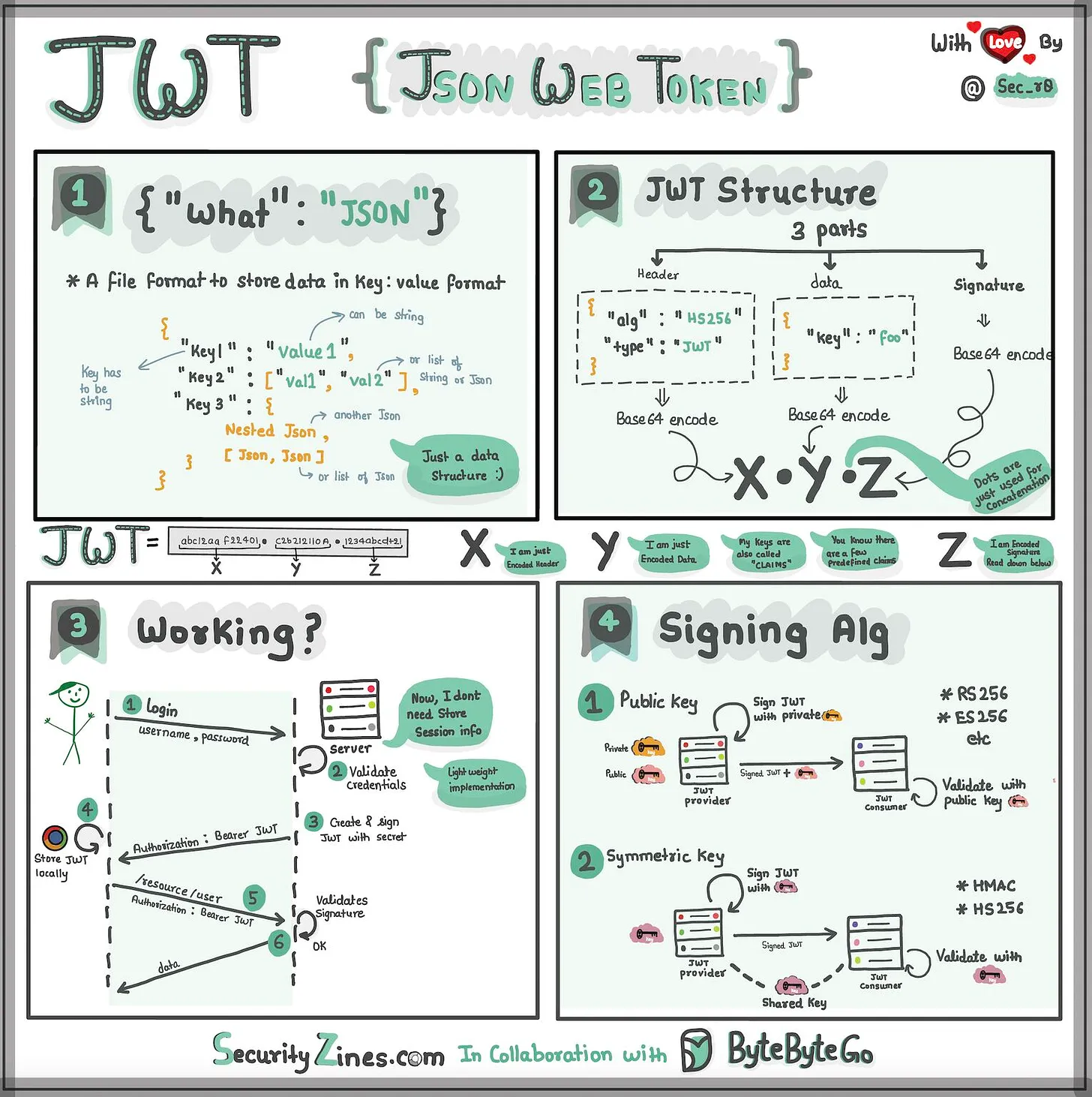
Session-Cookie AuthenticationSession-cookie authentication addresses HTTP basic access authentication's inability to track user login status. A session ID is generated to track the user's status during their visit. This session ID is recorded both server-side and in the client’s cookie. Bellow is the session cookie based interaction flow JWT TokenJWT VS Session tokensJSON Web Tokens (JWTs) and session tokens are both mechanisms used for authentication and authorization in web applications, but they have distinct characteristics and use cases. Here's a comparison of JWT tokens and session tokens: JWT (JSON Web Token):
Session Token:
Considerations:
In summary, JWTs and session tokens have different characteristics and are used in various contexts based on the specific needs of the application. The choice between them depends on factors such as the architecture, security requirements, and scalability of your application. |
OAuth 2.0 Standard Based AuthenticationOAuth 2.0 is a protocol that allows you to grant your application permission to access your data on another application. Let's use the Terrible Pun Joke case, to illustrate how OAuth 2.0 works. There are three main parties involved in OAuth 2.0:
Terrible Pun Jokes Application PerspectiveFrom the perspective of the Terrible Pun Jokes application, there is a partnership between itself and the gmail client authorization server.
User's Journey Using Terrible Pun JokesBelow is the user's journey when using the Terrible Pun Jokes application: In above Okta tutorial about OAuth and OPEN ID connect, what has not been mentioned is that there exists some form of trust relationship between the identity provider and the resource server. Perhaps the resource server can directly contact the identity provider to validate the presented code from the client, or the resource server has a verification key to verify the code validity directly. Bellow is the diagram describes the above statement 
|
OAuth and OPENID Connect (OIDC)Recap on OAuthOAuth is designed solely for authorization, allowing one application to grant access to data and features to another application. The OAuth flow provides the client with the necessary keys to access your data but does not reveal any information about the user's identity or characteristics. OPENID Connect (OIDC)OIDC is a layer built on top of OAuth 2.0, enhancing it with functionality related to user authentication and profile information. It enables the retrieval of information about the person who is logged in. For example, sign-in functionality using Google authentication. Single Sign-On (SSO)SSO, or "Single Sign-On," is an authentication process that allows users to access multiple applications or services using a single set of credentials, such as a username and password. Instead of needing separate login credentials for each application or service, SSO enables you to use the same login credentials for Google Mail and Google Docs, for instance. OIDC vs OAuthThe ID token used in OIDC is similar to a JWT token, allowing you to decode encoded information or verify its integrity. |














When we use various applications and websites, three essential security steps are continuously at play:
Bellow is a diagram where these methods applied in a typical website architecture
Overview
This article revisits the authentication related common senses.
The text was updated successfully, but these errors were encountered: