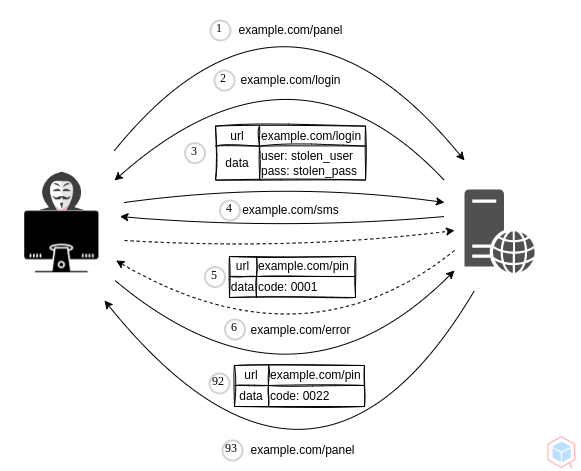
A threat actor may lunch brute force to the two-factor authentication (2FA) logic causing unauthorized access to the target.
- Threat actor has a stolen username and password pair for a vulnerable website
- Threat actor logs in and prompted with a four digits pin code that was sent to the victims mobile
- Threat actor lunches brute-force against and triggers the right pin code
Vary
- Gain unauthorized access
- Increase code length
- Limit pin code submissions
58a84977-90e1-4156-a555-8568e83115d0