-
Notifications
You must be signed in to change notification settings - Fork 85
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
MTNL Broadband and BSNL Broadband have refused to provide any information on ad injection on their platform #175
Comments
|
Related: #164. |
|
Right one the face of RTI and indian Internet Users |
|
@apsatwal i guess the certs mail box is full .......... |
|
Update 1: MTNL is also now injecting ads in both incoming and outgoing mails sent through their mail service. Outgoing is a common thing. A lot of webmail services add their signature line or at least they used to. But MTNL is going one step ahead and they are also tampering with INCOMING MAILS and insert their ads in them. Update 2: The modified mails are now linking to this domain: http://mtnlads.in/ which appears to be their upcoming gateway that might let you book ads for websites/mails that are tampered by MTNL. Update 3: I have prepared my appeal for the RTI and would be sending it tomorrow. If anyone want to see a copy, it can be accessed here. |
|
As per above website title "MTNL Advertisements made by Carizen" |
|
And their tech partner for ad-injection is Abeer Media and their subsidiary Adphonso. Just imagine how much private data is being leaked into private hands. Woo. |
|
In the injected ad links the utm_source is abeer |
|
Just an update. BSNL has also responded with the same excuse. Article 8(1)(d). https://drive.google.com/file/d/0B7GnL1EQD2WZX0dBNkZjSmhzeDQ/view |
|
https://drive.google.com/file/d/0B7GnL1EQD2WZbk9Sa0sxdkQzUTQ/view I filed an appeal with MTNL and they have responded to two questions now. They continue to block responses to other questions based on 8(1)(d). Based on this response... MTNL claims that absolutely no data is being collected during the process. They got this information through a certificate from the vendor. Now if we assume that the vendor is Abeer Media and the technology has been developed by Adphonso... This is a possible lie as Adphonso website clearly states that they collect tons of information to personalize ads. Of course, Adphonso could possibly disable the data collection feature on the platform. Question is... Is this enough? As long as they inject the ads, they can collect a lot of data whenever they want. They can track what websites are being visited by the user at any given time without any court order. This is in addition to all the revenue that is being made without caring about the user's security and privacy. Revenue which is being stolen from the content providers on the web including the MediaNama website which does not run on HTTPS. I am kind of clueless on what I can do now. I can possibly go to the CIC. Or file a complaint with TRAI. Both of which I have not done until now so I have no idea how to proceed. Hoping to get any kind of feedback and suggestions on what can be done now. Cheers. PS: I have also sent an appeal to BSNL in response to their non-answers. I assume they would be sending the exact response as MTNL as they did before. |
|
Got another letter from BSNL today. BSNL's Appellate authority states that the CPIO has applied his wisdom in answering/not-answering the questions so all is well. https://drive.google.com/open?id=0B7GnL1EQD2WZeWx2T3lZQW5mOFE PS: I am no longer pursuing this issue. I would update this thread when MTNL responds to the appeal I sent them few weeks ago. |
|
Here is new advertisement redirect by BSNL Here expected answer was NXDOMAIN |
|
@apsatwal check the server port which you are doing querying too |
|
MTNL also seems to be using phozeca these days. Can you tell the name of the ISP? |
|
It is Connect Broadband a subsidiary of Videocon Group |
|
Has anyone tried filing a complaint on the grounds of security and privacy? Asking them questions around commercials, scale of the programme and so on is what is getting stonewalled under the garb of trade secrets |
|
@anomalizer yes |
|
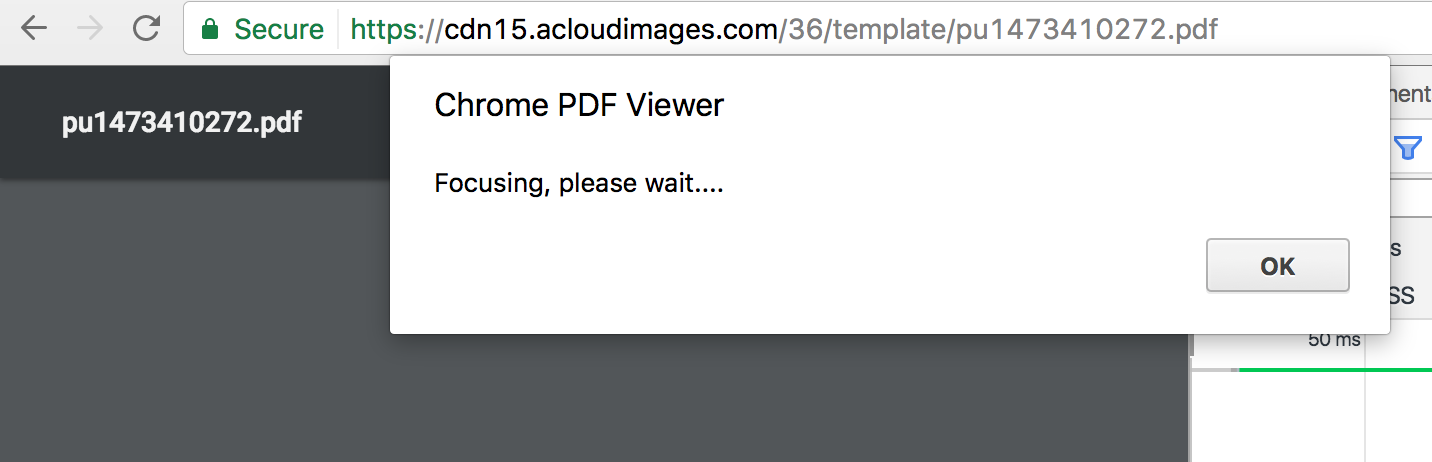
Fake Notification thanks to phozeca, and a redirect to infected pdf? Possible exploit of CVE-2016-1681? |
|
Many of these ad redirects go to pages that ask you to download malware installation files etc. Needless to say millions of BSNL subscribers might be infected with these malwares/viruses. I wonder, How is a govt owned company being able to do this and escape the public and laws of this country? |
|
@Sushubh Thank you for your efforts. Did you try approaching TRAI? |
|
Any updates on this? |
|
any Updates? |
|
This repository is for the 2015-16 campaign. It's no longer maintained. Please use the Internet Freedom Foundation's forum to discuss this and bring it to their attention for follow-up. |








I am not an expert on RTI but I tried asking a few questions. They rejected all of them on the basis of Section 8(1)(d) in The Right To Information Act, 2005.
I am attaching the RTI and the response here for reference. And looking forward to guidance on how this can be proceeded further.
The text was updated successfully, but these errors were encountered: