Maintainers
This module is maintained by the OCA.
- +
+
+
+ +
+
OCA, or the Odoo Community Association, is a nonprofit organization whose mission is to support the collaborative development of Odoo features and promote its widespread use.
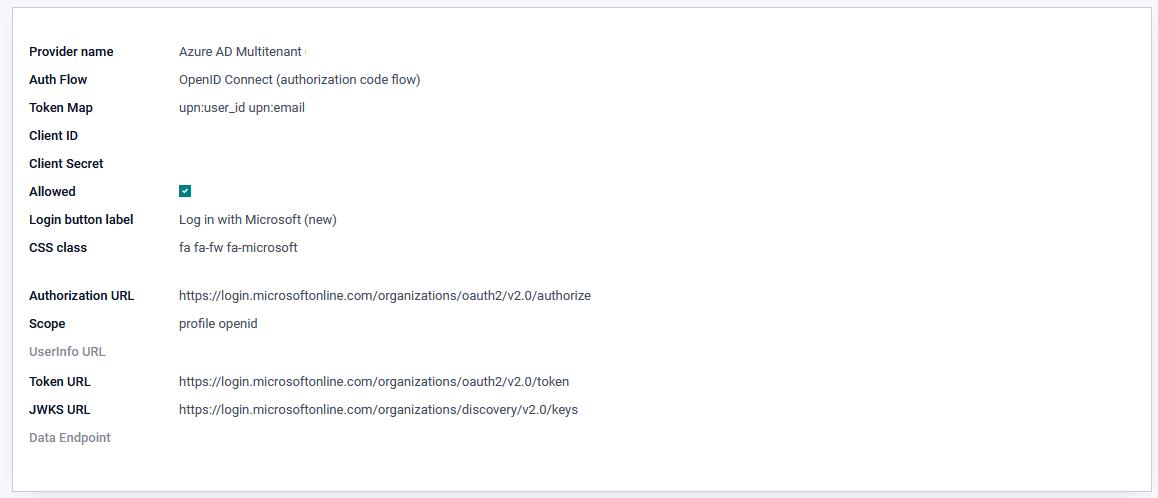
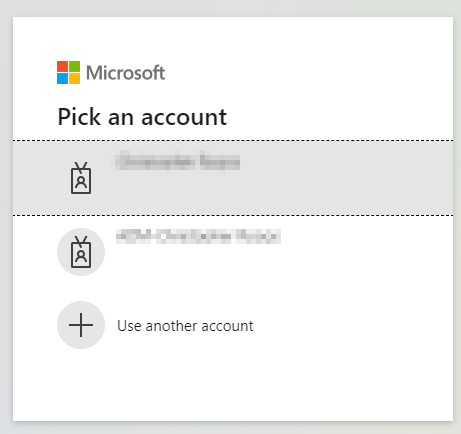
diff --git a/auth_oidc/static/description/oauth-microsoft_azure-select_account.png b/auth_oidc/static/description/oauth-microsoft_azure-select_account.png new file mode 100644 index 0000000000..a088777403 Binary files /dev/null and b/auth_oidc/static/description/oauth-microsoft_azure-select_account.png differ diff --git a/auth_oidc/tests/test_auth_oidc_auth_code.py b/auth_oidc/tests/test_auth_oidc_auth_code.py index a1a08b0a71..43a1ec6fff 100644 --- a/auth_oidc/tests/test_auth_oidc_auth_code.py +++ b/auth_oidc/tests/test_auth_oidc_auth_code.py @@ -71,7 +71,7 @@ def setUp(self): super().setUp() # search our test provider and bind the demo user to it self.provider_rec = self.env["auth.oauth.provider"].search( - [("client_id", "=", "auth_oidc-test")] + [("name", "=", "keycloak:8080 on localhost")] ) self.assertEqual(len(self.provider_rec), 1) @@ -83,8 +83,10 @@ def test_auth_link(self): ).write(dict(enabled=False)) with MockRequest(self.env): providers = OpenIDLogin().list_providers() - self.assertEqual(len(providers), 1) - auth_link = providers[0]["auth_link"] + self.assertEqual(len(providers), 2) + auth_link = list( + filter(lambda p: p["name"] == "keycloak:8080 on localhost", providers) + )[0]["auth_link"] assert auth_link.startswith(self.provider_rec.auth_endpoint) params = parse_qs(urlparse(auth_link).query) self.assertEqual(params["response_type"], ["code"]) @@ -95,6 +97,13 @@ def test_auth_link(self): self.assertTrue(params["nonce"]) self.assertTrue(params["state"]) self.assertEqual(params["redirect_uri"], [BASE_URL + "/auth_oauth/signin"]) + self.assertFalse("prompt" in params) + + auth_link_ms = list( + filter(lambda p: p["name"] == "Azure AD Multitenant", providers) + )[0]["auth_link"] + params = parse_qs(urlparse(auth_link_ms).query) + self.assertEqual(params["prompt"], ["select_account"]) def _prepare_login_test_user(self): user = self.env.ref("base.user_demo") diff --git a/auth_oidc/views/auth_oauth_provider.xml b/auth_oidc/views/auth_oauth_provider.xml index 90c931b417..c63f2cef60 100644 --- a/auth_oidc/views/auth_oauth_provider.xml +++ b/auth_oidc/views/auth_oauth_provider.xml @@ -19,6 +19,9 @@