From 994ea14f9ae28ae2147d0a88d068a0eb514c90cc Mon Sep 17 00:00:00 2001
From: MetaMask Bot <37885440+metamaskbot@users.noreply.github.com>
Date: Fri, 8 Mar 2024 09:09:21 -0500
Subject: [PATCH] Enabling MetaMask security code scanner (#149)
## Automated PR
This is automated Pull Request by Application Security team.
Please reach out to `@mm-application-security` slack if you have any
feedback or comments.
## Required Action
Prior to merging this pull request, please ensure the following has been
completed:
- [ ] The lines specifying `branches` correctly specifies this
repository's default branch (usually `main`).
- [ ] Any paths you would like to ignore have been added to the
`paths_ignored` configuration option (see
[setup](https://github.com/MetaMask/Security-Code-Scanner/blob/main/README.md#setup))
- [ ] Any existing CodeQL configuration has been disabled.
## What is the Security Code Scanner?
This pull request enables the [MetaMask Security Code
Scanner](https://github.com/metamask/Security-Code-Scanner/) GitHub
Action. This action runs on each pull request, and will flag potential
vulnerabilities as a review comment. It will also scan this repository's
default branch, and log any findings in this repository's [Code Scanning
Alerts
Tab](https://github.com/metamask/template-snap-monorepo/security/code-scanning).
 The action itself runs various static analysis engines behind the
scenes. Currently, it is only running GitHub's CodeQL engine. For this
reason, we recommend disabling any existing CodeQL configuration your
repository may have.
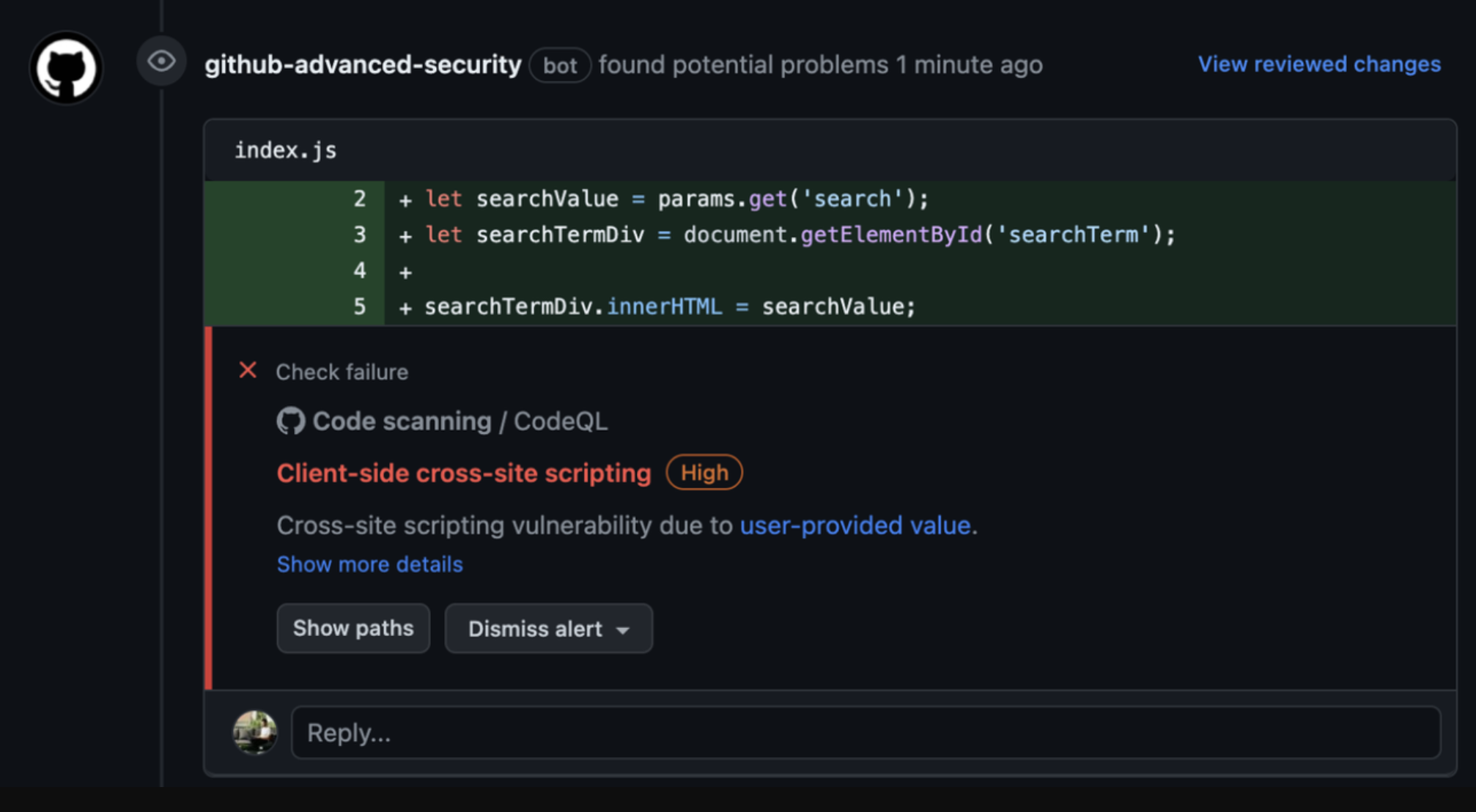
## How do I interact with the tool?
Every finding raised by the Security Code Scanner will present context
behind the potential vulnerability identified, and allow the developer
to fix, or dismiss it.
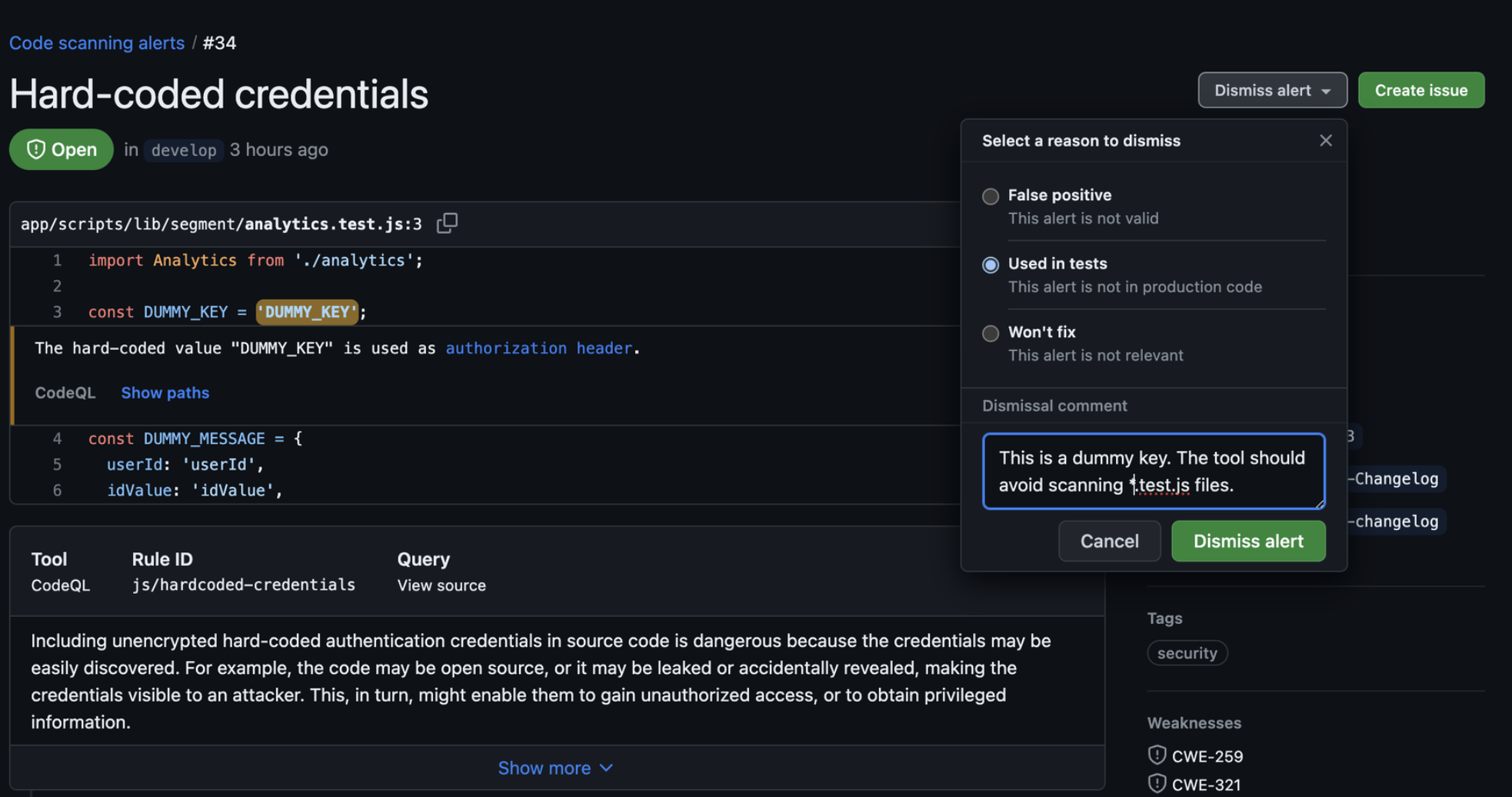
The finding will automatically be dismissed by pushing a commit that
fixes the identified issue, or by manually dismissing the alert using
the button in GitHub's UI. If dismissing an alert manually, please add
any additional context surrounding the reason for dismissal, as this
informs our decision to disable, or improve any poor performing rules.
The action itself runs various static analysis engines behind the
scenes. Currently, it is only running GitHub's CodeQL engine. For this
reason, we recommend disabling any existing CodeQL configuration your
repository may have.
## How do I interact with the tool?
Every finding raised by the Security Code Scanner will present context
behind the potential vulnerability identified, and allow the developer
to fix, or dismiss it.
The finding will automatically be dismissed by pushing a commit that
fixes the identified issue, or by manually dismissing the alert using
the button in GitHub's UI. If dismissing an alert manually, please add
any additional context surrounding the reason for dismissal, as this
informs our decision to disable, or improve any poor performing rules.
 For more configuration options, please review the tool's
[README](https://github.com/MetaMask/Security-Code-Scanner/blob/main/README.md).
For any additional questions, please reach out to
`@mm-application-security` slack.
---
.github/workflows/security-code-scanner.yml | 43 +++++++++++++++++++++
1 file changed, 43 insertions(+)
create mode 100644 .github/workflows/security-code-scanner.yml
diff --git a/.github/workflows/security-code-scanner.yml b/.github/workflows/security-code-scanner.yml
new file mode 100644
index 00000000..ced04497
--- /dev/null
+++ b/.github/workflows/security-code-scanner.yml
@@ -0,0 +1,43 @@
+name: 'MetaMask Security Code Scanner'
+
+on:
+ push:
+ branches: ['main']
+ pull_request:
+ branches: ['main']
+
+jobs:
+ run-security-scan:
+ runs-on: ubuntu-latest
+ permissions:
+ actions: read
+ contents: read
+ security-events: write
+ steps:
+ - name: MetaMask Security Code Scanner
+ uses: MetaMask/Security-Code-Scanner@main
+ with:
+ repo: ${{ github.repository }}
+ paths_ignored: |
+ .storybook/
+ '**/__snapshots__/'
+ '**/*.snap'
+ '**/*.stories.js'
+ '**/*.stories.tsx'
+ '**/*.test.browser.ts*'
+ '**/*.test.js*'
+ '**/*.test.ts*'
+ '**/fixtures/'
+ '**/jest.config.js'
+ '**/jest.environment.js'
+ '**/mocks/'
+ '**/test*/'
+ docs/
+ e2e/
+ merged-packages/
+ node_modules
+ storybook/
+ test*/
+ rules_excluded: example
+ project_metrics_token: ${{ secrets.SECURITY_SCAN_METRICS_TOKEN }}
+ slack_webhook: ${{ secrets.APPSEC_BOT_SLACK_WEBHOOK }}
For more configuration options, please review the tool's
[README](https://github.com/MetaMask/Security-Code-Scanner/blob/main/README.md).
For any additional questions, please reach out to
`@mm-application-security` slack.
---
.github/workflows/security-code-scanner.yml | 43 +++++++++++++++++++++
1 file changed, 43 insertions(+)
create mode 100644 .github/workflows/security-code-scanner.yml
diff --git a/.github/workflows/security-code-scanner.yml b/.github/workflows/security-code-scanner.yml
new file mode 100644
index 00000000..ced04497
--- /dev/null
+++ b/.github/workflows/security-code-scanner.yml
@@ -0,0 +1,43 @@
+name: 'MetaMask Security Code Scanner'
+
+on:
+ push:
+ branches: ['main']
+ pull_request:
+ branches: ['main']
+
+jobs:
+ run-security-scan:
+ runs-on: ubuntu-latest
+ permissions:
+ actions: read
+ contents: read
+ security-events: write
+ steps:
+ - name: MetaMask Security Code Scanner
+ uses: MetaMask/Security-Code-Scanner@main
+ with:
+ repo: ${{ github.repository }}
+ paths_ignored: |
+ .storybook/
+ '**/__snapshots__/'
+ '**/*.snap'
+ '**/*.stories.js'
+ '**/*.stories.tsx'
+ '**/*.test.browser.ts*'
+ '**/*.test.js*'
+ '**/*.test.ts*'
+ '**/fixtures/'
+ '**/jest.config.js'
+ '**/jest.environment.js'
+ '**/mocks/'
+ '**/test*/'
+ docs/
+ e2e/
+ merged-packages/
+ node_modules
+ storybook/
+ test*/
+ rules_excluded: example
+ project_metrics_token: ${{ secrets.SECURITY_SCAN_METRICS_TOKEN }}
+ slack_webhook: ${{ secrets.APPSEC_BOT_SLACK_WEBHOOK }}
 The action itself runs various static analysis engines behind the
scenes. Currently, it is only running GitHub's CodeQL engine. For this
reason, we recommend disabling any existing CodeQL configuration your
repository may have.
## How do I interact with the tool?
Every finding raised by the Security Code Scanner will present context
behind the potential vulnerability identified, and allow the developer
to fix, or dismiss it.
The finding will automatically be dismissed by pushing a commit that
fixes the identified issue, or by manually dismissing the alert using
the button in GitHub's UI. If dismissing an alert manually, please add
any additional context surrounding the reason for dismissal, as this
informs our decision to disable, or improve any poor performing rules.
The action itself runs various static analysis engines behind the
scenes. Currently, it is only running GitHub's CodeQL engine. For this
reason, we recommend disabling any existing CodeQL configuration your
repository may have.
## How do I interact with the tool?
Every finding raised by the Security Code Scanner will present context
behind the potential vulnerability identified, and allow the developer
to fix, or dismiss it.
The finding will automatically be dismissed by pushing a commit that
fixes the identified issue, or by manually dismissing the alert using
the button in GitHub's UI. If dismissing an alert manually, please add
any additional context surrounding the reason for dismissal, as this
informs our decision to disable, or improve any poor performing rules.
 For more configuration options, please review the tool's
[README](https://github.com/MetaMask/Security-Code-Scanner/blob/main/README.md).
For any additional questions, please reach out to
`@mm-application-security` slack.
---
.github/workflows/security-code-scanner.yml | 43 +++++++++++++++++++++
1 file changed, 43 insertions(+)
create mode 100644 .github/workflows/security-code-scanner.yml
diff --git a/.github/workflows/security-code-scanner.yml b/.github/workflows/security-code-scanner.yml
new file mode 100644
index 00000000..ced04497
--- /dev/null
+++ b/.github/workflows/security-code-scanner.yml
@@ -0,0 +1,43 @@
+name: 'MetaMask Security Code Scanner'
+
+on:
+ push:
+ branches: ['main']
+ pull_request:
+ branches: ['main']
+
+jobs:
+ run-security-scan:
+ runs-on: ubuntu-latest
+ permissions:
+ actions: read
+ contents: read
+ security-events: write
+ steps:
+ - name: MetaMask Security Code Scanner
+ uses: MetaMask/Security-Code-Scanner@main
+ with:
+ repo: ${{ github.repository }}
+ paths_ignored: |
+ .storybook/
+ '**/__snapshots__/'
+ '**/*.snap'
+ '**/*.stories.js'
+ '**/*.stories.tsx'
+ '**/*.test.browser.ts*'
+ '**/*.test.js*'
+ '**/*.test.ts*'
+ '**/fixtures/'
+ '**/jest.config.js'
+ '**/jest.environment.js'
+ '**/mocks/'
+ '**/test*/'
+ docs/
+ e2e/
+ merged-packages/
+ node_modules
+ storybook/
+ test*/
+ rules_excluded: example
+ project_metrics_token: ${{ secrets.SECURITY_SCAN_METRICS_TOKEN }}
+ slack_webhook: ${{ secrets.APPSEC_BOT_SLACK_WEBHOOK }}
For more configuration options, please review the tool's
[README](https://github.com/MetaMask/Security-Code-Scanner/blob/main/README.md).
For any additional questions, please reach out to
`@mm-application-security` slack.
---
.github/workflows/security-code-scanner.yml | 43 +++++++++++++++++++++
1 file changed, 43 insertions(+)
create mode 100644 .github/workflows/security-code-scanner.yml
diff --git a/.github/workflows/security-code-scanner.yml b/.github/workflows/security-code-scanner.yml
new file mode 100644
index 00000000..ced04497
--- /dev/null
+++ b/.github/workflows/security-code-scanner.yml
@@ -0,0 +1,43 @@
+name: 'MetaMask Security Code Scanner'
+
+on:
+ push:
+ branches: ['main']
+ pull_request:
+ branches: ['main']
+
+jobs:
+ run-security-scan:
+ runs-on: ubuntu-latest
+ permissions:
+ actions: read
+ contents: read
+ security-events: write
+ steps:
+ - name: MetaMask Security Code Scanner
+ uses: MetaMask/Security-Code-Scanner@main
+ with:
+ repo: ${{ github.repository }}
+ paths_ignored: |
+ .storybook/
+ '**/__snapshots__/'
+ '**/*.snap'
+ '**/*.stories.js'
+ '**/*.stories.tsx'
+ '**/*.test.browser.ts*'
+ '**/*.test.js*'
+ '**/*.test.ts*'
+ '**/fixtures/'
+ '**/jest.config.js'
+ '**/jest.environment.js'
+ '**/mocks/'
+ '**/test*/'
+ docs/
+ e2e/
+ merged-packages/
+ node_modules
+ storybook/
+ test*/
+ rules_excluded: example
+ project_metrics_token: ${{ secrets.SECURITY_SCAN_METRICS_TOKEN }}
+ slack_webhook: ${{ secrets.APPSEC_BOT_SLACK_WEBHOOK }}